Question 476
A security architect is designing a new infrastructure using both type 1 and type 2 virtual machines. In addition to the normal complement of security controls (e.g. antivirus, host hardening, HIPS/NIDS) the security architect needs to implement a mechanism to securely store cryptographic keys used to sign code and code modules on the VMs. Which of the following will meet this goal without requiring any hardware pass-through implementations?
Question 477
Given the following:
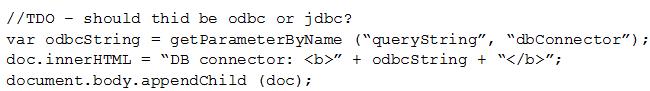
Which of the following vulnerabilities is present in the above code snippet?

Which of the following vulnerabilities is present in the above code snippet?
Question 478
A manufacturing company recently recovered from an attack on its ICS devices. It has since reduced the attack surface by isolating the affected components. The company now wants to implement detection capabilities. It is considering a system that is based on machine learning.
Which of the following features would BEST describe the driver to adopt such nascent technology over mainstream commercial IDSs?
Which of the following features would BEST describe the driver to adopt such nascent technology over mainstream commercial IDSs?
Question 479
A security analyst is reviewing logs and discovers that a company-owned computer issued to an employee is generating many alerts and analyst continues to review the log events and discovers that a non-company-owned device from a different, unknown IP address is general same events. The analyst informs the manager of these finding, and the manager explains that these activities are already known and . . . ongoing simulation. Given this scenario, which of the following roles are the analyst, the employee, and the manager fillings?
Question 480
A company is acquiring incident response and forensic assistance from a managed security service provider in the event of a data breach. The company has selected a partner and must now provide required documents to be reviewed and evaluated. Which of the following documents would BEST protect the company and ensure timely assistance? (Choose two.)

