Question 466
A company recently migrated to a SaaS-based email solution. The solution is configured as follows.
* Passwords are synced to the cloud to allow for SSO
* Cloud-based antivirus is enabled
* Cloud-based anti-spam is enabled
* Subscription-based blacklist is enabled
Although the above controls are enabled, the company's security administrator is unable to detect an account compromise caused by phishing attacks in a timely fashion because email logs are not immediately available to review. Which of the following would allow the company to gam additional visibility and reduce additional costs? (Select TWO)
* Passwords are synced to the cloud to allow for SSO
* Cloud-based antivirus is enabled
* Cloud-based anti-spam is enabled
* Subscription-based blacklist is enabled
Although the above controls are enabled, the company's security administrator is unable to detect an account compromise caused by phishing attacks in a timely fashion because email logs are not immediately available to review. Which of the following would allow the company to gam additional visibility and reduce additional costs? (Select TWO)
Question 467
A large enterprise acquires another company which uses antivirus from a different vendor. The CISO has requested that data feeds from the two different antivirus platforms be combined in a way that allows management to assess and rate the overall effectiveness of antivirus across the entire organization. Which of the following tools can BEST meet the CISO's requirement?
Question 468
A deployment manager is working with a software development group to assess the security of a new version of the organization's internally developed ERP tool. The organization prefers to not perform assessment activities following deployment, instead focusing on assessing security throughout the life cycle. Which of the following methods would BEST assess the security of the product?
Question 469
A security analyst sees some suspicious entries in a log file from a web server website, which has a form that allows customers to leave feedback on the company's products. The analyst believes a malicious actor is scanning the web form. To know which security controls to put in place, the analyst first needs to determine the type of activity occurring to design a control. Given the log below:
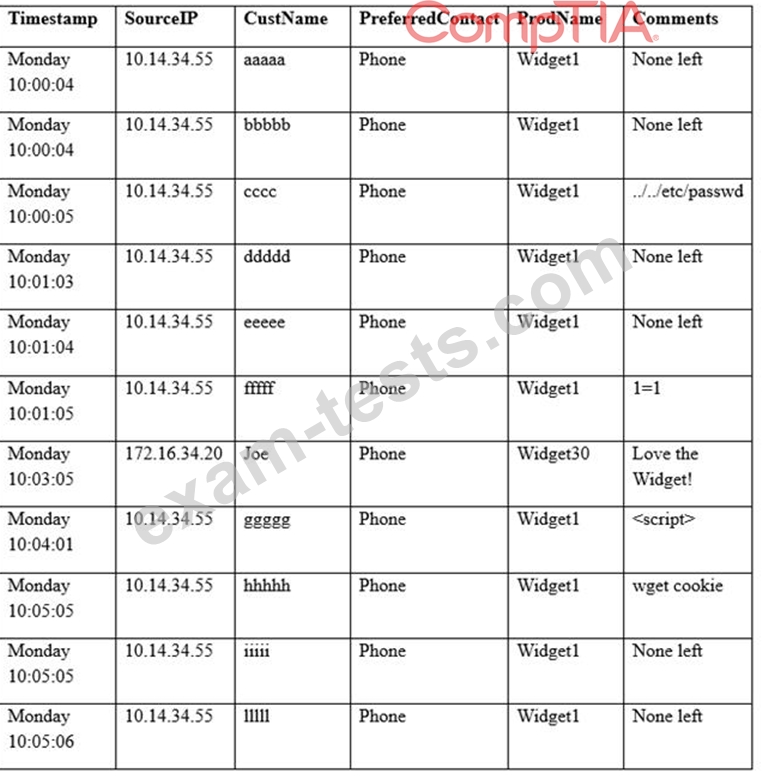
Which of the following is the MOST likely type of activity occurring?

Which of the following is the MOST likely type of activity occurring?
Question 470
The Information Security Officer (ISO) believes that the company has been targeted by cybercriminals and it is under a cyber attack. Internal services that are normally available to the public via the Internet are inaccessible, and employees in the office are unable to browse the Internet. The senior security engineer starts by reviewing the bandwidth at the border router, and notices that the incoming bandwidth on the router's external interface is maxed out. The security engineer then inspects the following piece of log to try and determine the reason for the downtime, focusing on the company's external router's IP which is 128.20.176.19:
11:16:22.110343 IP 90.237.31.27.19 > 128.20.176.19.19: UDP, length 1400
11:16:22.110351 IP 23.27.112.200.19 > 128.20.176.19.19: UDP, length
1400
11:16:22.110358 IP 192.200.132.213.19 > 128.20.176.19.19: UDP, length
1400
11:16:22.110402 IP 70.192.2.55.19 > 128.20.176.19.19: UDP, length 1400
11:16:22.110406 IP 112.201.7.39.19 > 128.20.176.19.19: UDP, length 1400 Which of the following describes the findings the senior security engineer should report to the ISO and the BEST solution for service restoration?
11:16:22.110343 IP 90.237.31.27.19 > 128.20.176.19.19: UDP, length 1400
11:16:22.110351 IP 23.27.112.200.19 > 128.20.176.19.19: UDP, length
1400
11:16:22.110358 IP 192.200.132.213.19 > 128.20.176.19.19: UDP, length
1400
11:16:22.110402 IP 70.192.2.55.19 > 128.20.176.19.19: UDP, length 1400
11:16:22.110406 IP 112.201.7.39.19 > 128.20.176.19.19: UDP, length 1400 Which of the following describes the findings the senior security engineer should report to the ISO and the BEST solution for service restoration?

