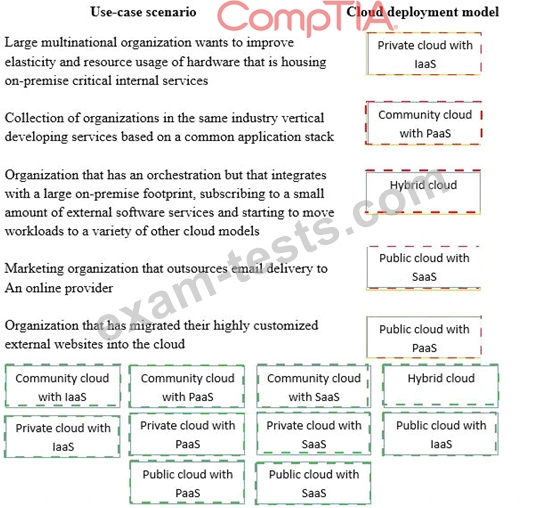
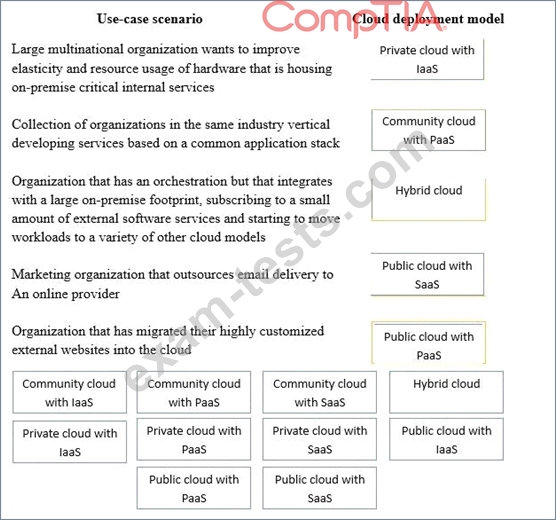
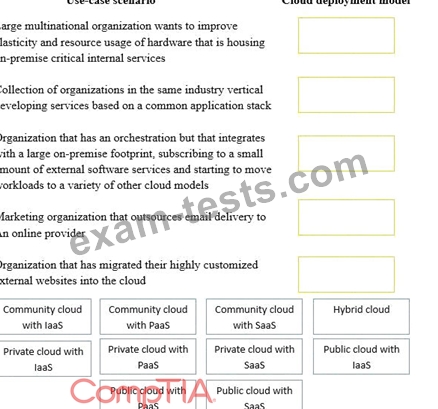
Question 46
Drag and drop the cloud deployment model to the associated use-case scenario. Options may be used only once or not at all.

Question 47
Which of the following BEST represents a risk associated with merging two enterprises during an
acquisition?
acquisition?
Question 48
A managed service provider is designing a log aggregation service for customers who no longer want to manage an internal SIEM infrastructure. The provider expects that customers will send all types of logs to them, and that log files could contain very sensitive entries. Customers have indicated they want on- premises and cloud-based infrastructure logs to be stored in this new service. An engineer, who is designing the new service, is deciding how to segment customers.
Which of the following is the BEST statement for the engineer to take into consideration?
Which of the following is the BEST statement for the engineer to take into consideration?
Question 49
An analyst is testing the security of a server and attempting to infiltrate the network. The analyst is able to obtain the following output after running some tools on the server.
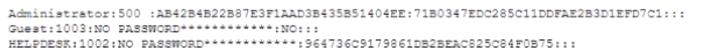
Which of the following will the analyst most likely do NEXT?

Which of the following will the analyst most likely do NEXT?
Question 50
Executive management is asking for a new manufacturing control and workflow automation solution. This application will facilitate management of proprietary information and closely guarded corporate trade secrets.
The information security team has been a part of the department meetings and come away with the following notes:
Human resources would like complete access to employee data stored in the application. They would like automated data interchange with the employee management application, a cloud- based SaaS application.
Sales is asking for easy order tracking to facilitate feedback to customers.
Legal is asking for adequate safeguards to protect trade secrets. They are also concerned with data ownership questions and legal jurisdiction.
Manufacturing is asking for ease of use. Employees working the assembly line cannot be bothered with additional steps or overhead. System interaction needs to be quick and easy.
Quality assurance is concerned about managing the end product and tracking overall performance of the product being produced. They would like read-only access to the entire workflow process for monitoring and baselining.
The favored solution is a user friendly software application that would be hosted onsite. It has extensive ACL functionality, but also has readily available APIs for extensibility. It supports read- only access, kiosk automation, custom fields, and data encryption.
Which of the following departments' request is in contrast to the favored solution?
The information security team has been a part of the department meetings and come away with the following notes:
Human resources would like complete access to employee data stored in the application. They would like automated data interchange with the employee management application, a cloud- based SaaS application.
Sales is asking for easy order tracking to facilitate feedback to customers.
Legal is asking for adequate safeguards to protect trade secrets. They are also concerned with data ownership questions and legal jurisdiction.
Manufacturing is asking for ease of use. Employees working the assembly line cannot be bothered with additional steps or overhead. System interaction needs to be quick and easy.
Quality assurance is concerned about managing the end product and tracking overall performance of the product being produced. They would like read-only access to the entire workflow process for monitoring and baselining.
The favored solution is a user friendly software application that would be hosted onsite. It has extensive ACL functionality, but also has readily available APIs for extensibility. It supports read- only access, kiosk automation, custom fields, and data encryption.
Which of the following departments' request is in contrast to the favored solution?