Question 56
Which of the following is the GREATEST security concern with respect to BYOD?
Question 57
A security analyst sees some suspicious entries in a log file from a web server website, which has a form that allows customers to leave feedback on the company's products. The analyst believes a malicious actor is scanning the web form. To know which security controls to put in place, the analyst first needs to determine the type of activity occurring to design a control. Given the log below:
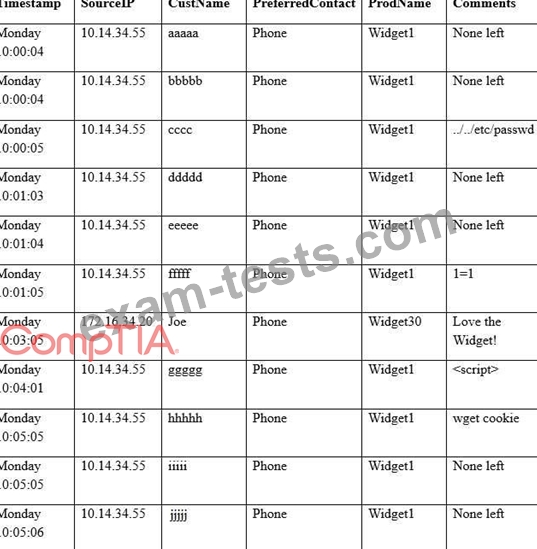
Which of the following is the MOST likely type of activity occurring?

Which of the following is the MOST likely type of activity occurring?
Question 58
A security engineer is assisting a developer with input validation, and they are studying the following code block:
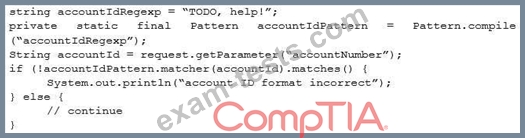
The security engineer wants to ensure strong input validation is in place for customer-provided account identifiers. These identifiers are ten-digit numbers. The developer wants to ensure input validation is fast because a large number of people use the system.
Which of the following would be the BEST advice for the security engineer to give to the developer?

The security engineer wants to ensure strong input validation is in place for customer-provided account identifiers. These identifiers are ten-digit numbers. The developer wants to ensure input validation is fast because a large number of people use the system.
Which of the following would be the BEST advice for the security engineer to give to the developer?
Question 59
A company has completed the implementation of technical and management controls as required by its adopted security, ponies and standards. The implementation took two years and consumed s the budget approved to security projects. The board has denied any further requests for additional budget. Which of the following should the company do to address the residual risk?
Question 60
An IT manager is concerned about the cost of implementing a web filtering solution in an effort to mitigate the risks associated with malware and resulting data leakage. Given that the ARO is twice per year, the ALE resulting from a data leak is $25,000 and the ALE after implementing the web filter is $15,000. The web filtering solution will cost the organization $10,000 per year. Which of the following values is the single loss expectancy of a data leakage event after implementing the web filtering solution?

