Question 66
Following a recent network intrusion, a company wants to determine the current security awareness of all of its employees. Which of the following is the BEST way to test awareness?
Question 67
Lab Simulation
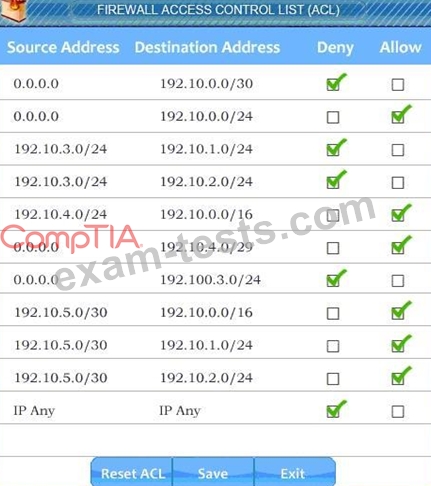
Company A has noticed abnormal behavior targeting their SQL server on the network from a rogue IP address.
The company uses the following internal IP address ranges:
192.10.1.0/24 for the corporate site and 192.10.2.0/24 for the remote site.
The Telco router interface uses the 192.10.5.0/30 IP range.
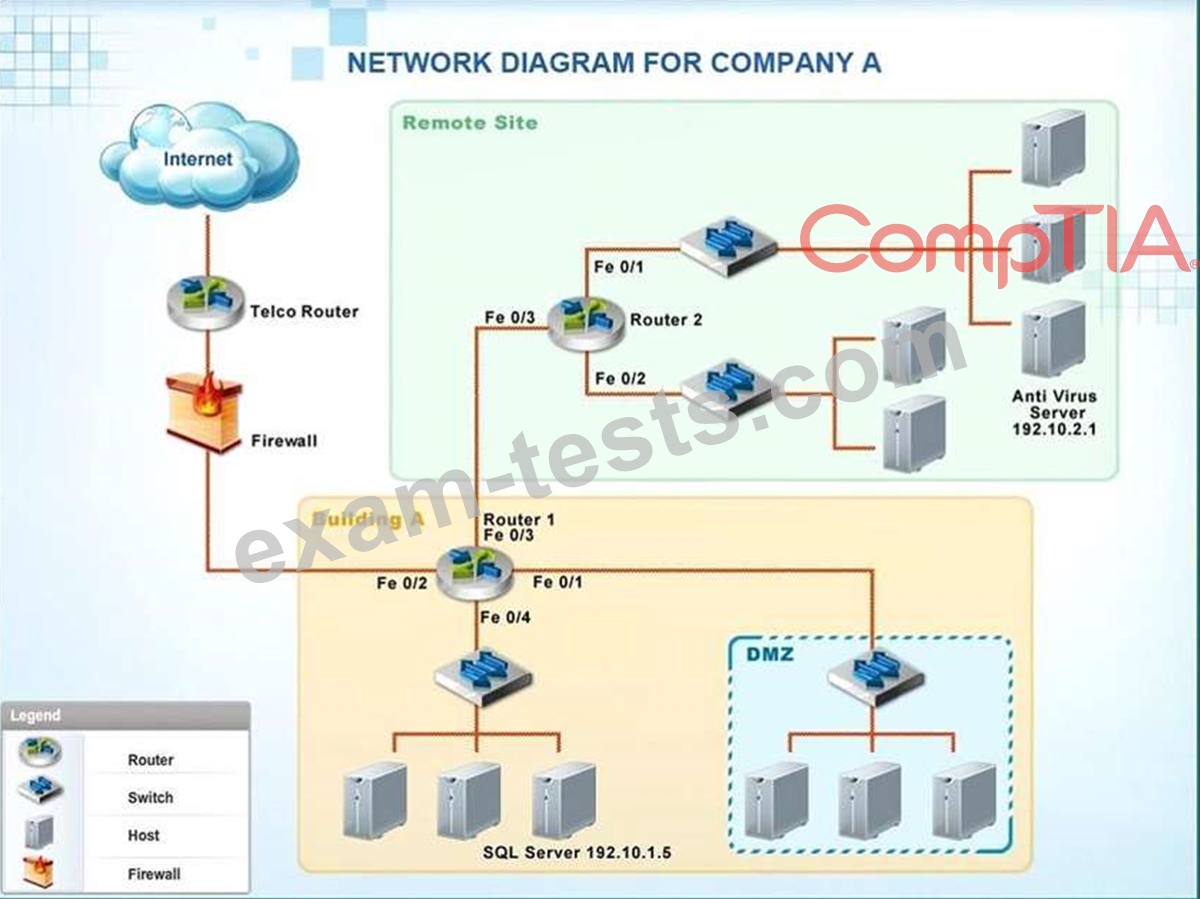
Instructions: Click on the simulation button to refer to the Network Diagram for Company A.
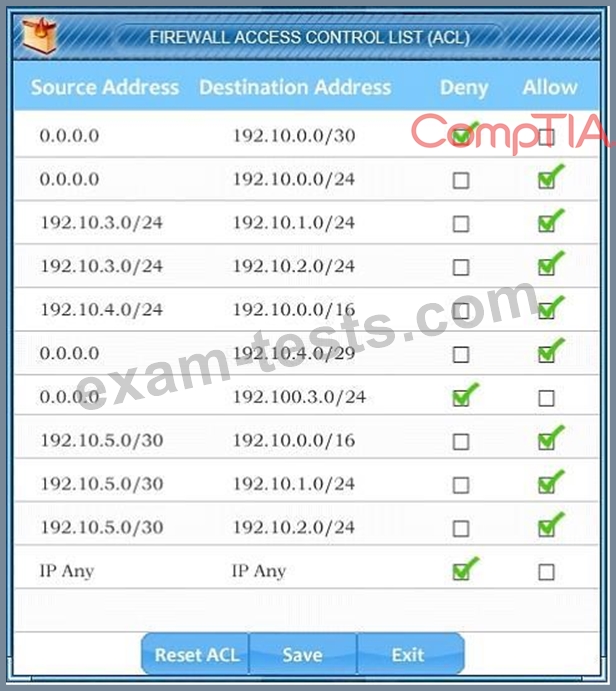
Click on Router 1, Router 2, and the Firewall to evaluate and configure each device.
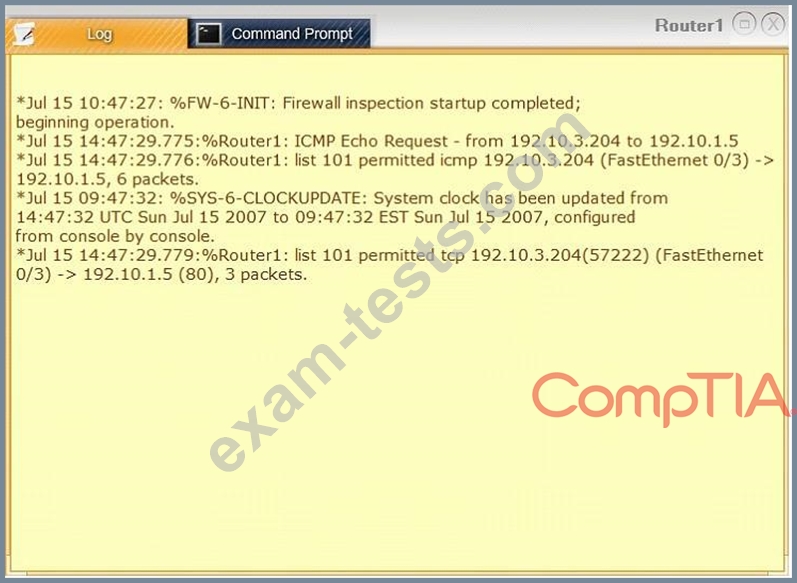
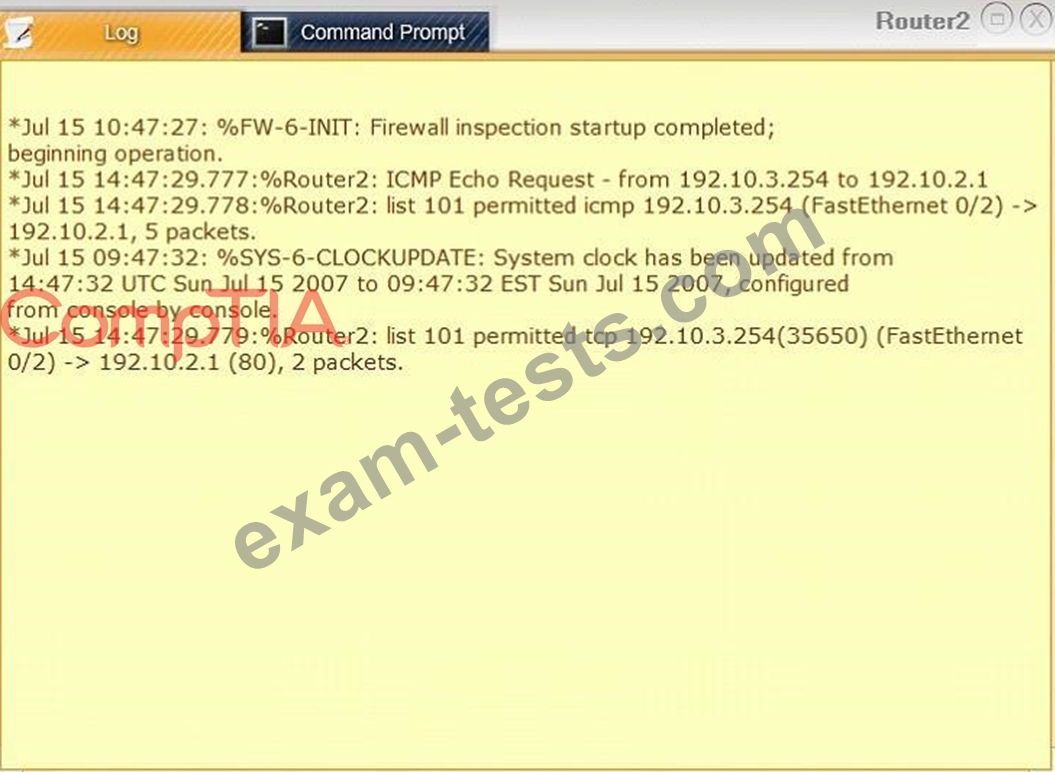
Task 1: Display and examine the logs and status of Router 1, Router 2, and Firewall interfaces.
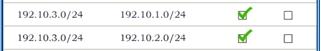
Task 2: Reconfigure the appropriate devices to prevent the attacks from continuing to target the SQL server and other servers on the corporate network.
Company A has noticed abnormal behavior targeting their SQL server on the network from a rogue IP address.
The company uses the following internal IP address ranges:
192.10.1.0/24 for the corporate site and 192.10.2.0/24 for the remote site.
The Telco router interface uses the 192.10.5.0/30 IP range.
Instructions: Click on the simulation button to refer to the Network Diagram for Company A.
Click on Router 1, Router 2, and the Firewall to evaluate and configure each device.
Task 1: Display and examine the logs and status of Router 1, Router 2, and Firewall interfaces.
Task 2: Reconfigure the appropriate devices to prevent the attacks from continuing to target the SQL server and other servers on the corporate network.






Question 68
A large, multinational company currently has two separate databases One is used for ERP while the second is used for CRM To consolidate services and infrastructure, it is proposed to combine the databases The company's compliance manager is asked to review the proposal and is concerned about this integration Which of the following would pose the MOST concern to the compliance manager?
Question 69
A critical system audit shows that the payroll system is not meeting security policy due to missing OS security patches. Upon further review, it appears that the system is not being patched at all. The vendor states that the system is only supported on the current OS patch level. Which of the following compensating controls should be used to mitigate the vulnerability of missing OS patches on this system?
Question 70
Confidential information related to Application A.
Application B and Project X appears to have been leaked to a competitor. After consulting with the legal team, the IR team is advised to take immediate action to preserve evidence for possible litigation and criminal charges.
While reviewing the rights and group ownership of the data involved in the breach, the IR team inspects the following distribution group access lists:
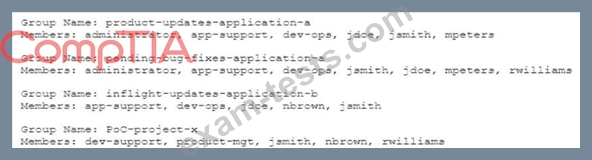
Which of the following actions should the IR team take FIRST?
Application B and Project X appears to have been leaked to a competitor. After consulting with the legal team, the IR team is advised to take immediate action to preserve evidence for possible litigation and criminal charges.
While reviewing the rights and group ownership of the data involved in the breach, the IR team inspects the following distribution group access lists:

Which of the following actions should the IR team take FIRST?