Question 51
A security engineer is analyzing an application during a security assessment to ensure it is configured to protect against common threats. Given the output below:
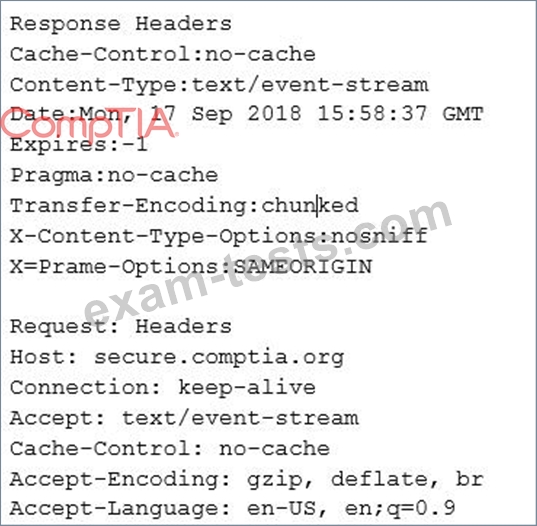
Which of the following tools did the security engineer MOST likely use to generate this output?

Which of the following tools did the security engineer MOST likely use to generate this output?
Question 52
An organization has implemented an Agile development process for front end web application development. A new security architect has just joined the company and wants to integrate security activities into the SDLC.
Which of the following activities MUST be mandated to ensure code quality from a security perspective?
(Select TWO).
Which of the following activities MUST be mandated to ensure code quality from a security perspective?
(Select TWO).
Question 53
An external penetration tester compromised one of the client organization's authentication servers and retrieved the password database. Which of the following methods allows the penetration tester to MOST efficiently use any obtained administrative credentials on the client organization's other systems, without impacting the integrity of any of the systems?
Question 54
A company wants to confirm sufficient executable space protection is in place for scenarios in which malware may be attempting buffer overflow attacks. Which of the following should the security engineer check?
Question 55
Providers at a healthcare system with many geographically dispersed clinics have been fined five times this year after an auditor received notice of the following SMS messages:
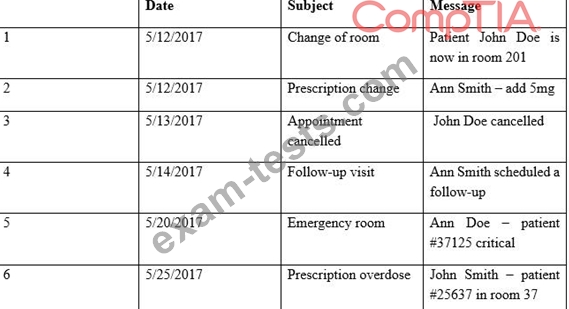
Which of the following represents the BEST solution for preventing future fines?

Which of the following represents the BEST solution for preventing future fines?

