Question 171
A forensics analyst suspects that a breach has occurred. Security logs show the company's OS patch system may be compromised, and it is serving patches that contain a zero-day exploit and backdoor. The analyst extracts an executable file from a packet capture of communication between a client computer and the patch server. Which of the following should the analyst use to confirm this suspicion?
Question 172
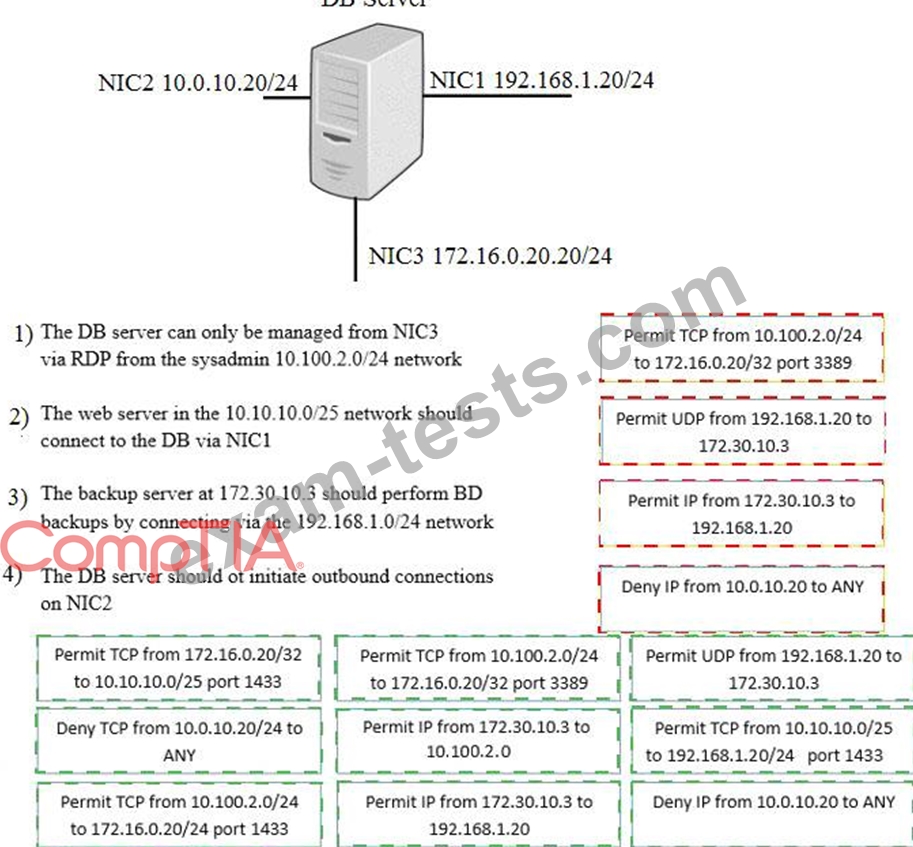
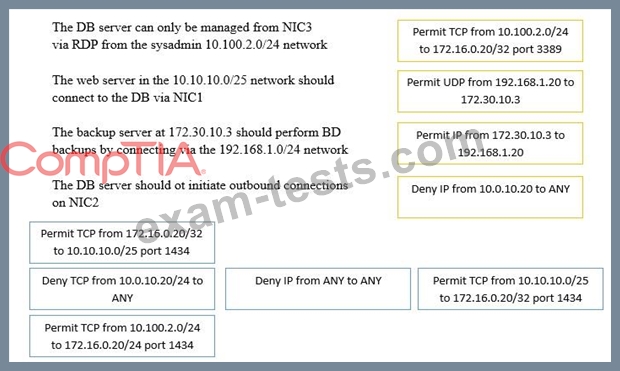
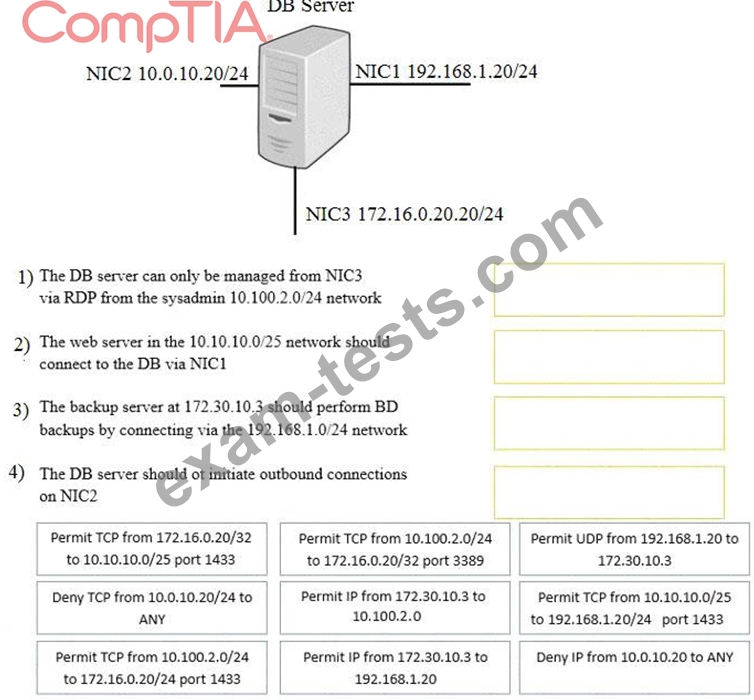
A security administrator must configure the database server shown below to comply with the four requirements listed. Drag and drop the appropriate ACL that should be configured on the database server to its corresponding requirement. Answer options may be used once or not at all.

Question 173
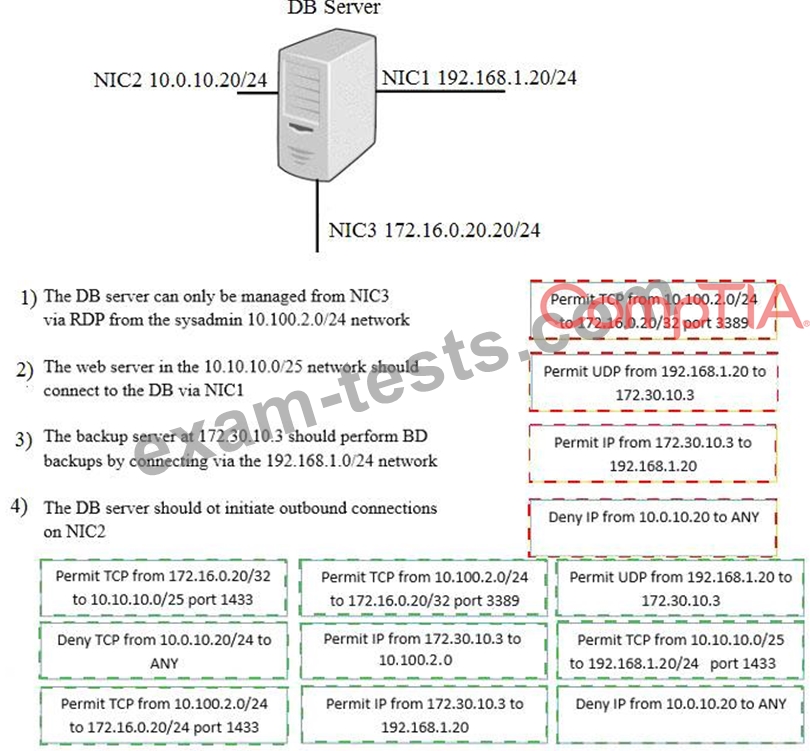
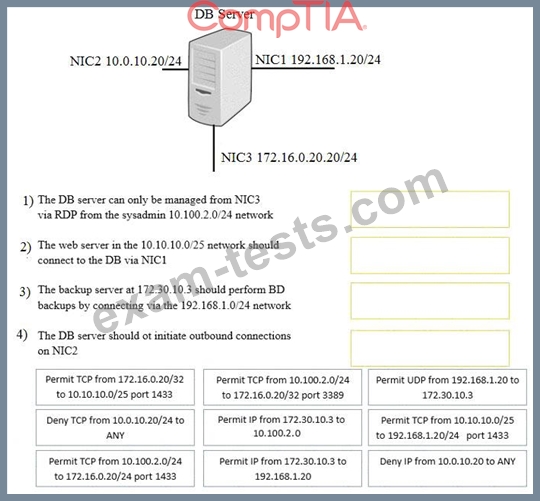
A security administrator must configure the database server shown below to comply with the four requirements listed. Drag and drop the appropriate ACL that should be configured on the database server to its corresponding requirement. Answer options may be used once or not at all.

Question 174
Given the following code snippet:
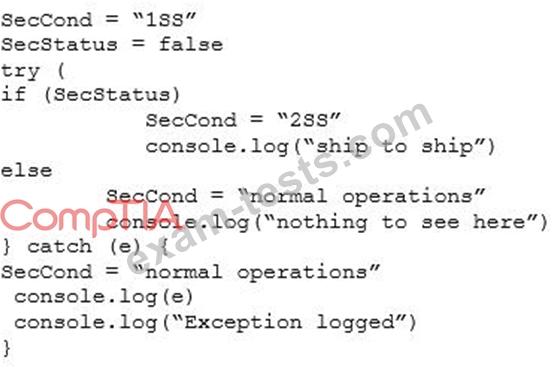
Which of the following failure modes would the code exhibit?

Which of the following failure modes would the code exhibit?
Question 175
A security officer is reviewing the following evidence associated with a recent penetration test:

The lest results show this host is vulnerable. The security officer investigates further and determines device was connected to the network by a user without permission. Which of the following is the MOST appropriate recommendation for the security officer to make?

The lest results show this host is vulnerable. The security officer investigates further and determines device was connected to the network by a user without permission. Which of the following is the MOST appropriate recommendation for the security officer to make?