Question 156
During a sprint, developers are responsible for ensuring the expected outcome of a change is thoroughly evaluated for any security impacts. Any impacts must be reported to the team lead. Before changes are made to the source code, which of the following MUST be performed to provide the required information to the team lead?
Question 157
The Chief Financial Officer (CFO) of a major hospital system has received a ransom letter that demands a large sum of cryptocurrency be transferred to an anonymous account. If the transfer does not take place within ten hours, the letter states that patient information will be released on the dark web. A partial listing of recent patients is included in the letter. This is the first indication that a breach took place. Which of the following steps should be done FIRST?
Question 158
Compliance with company policy requires a quarterly review of firewall rules. You are asked to conduct a review on the internal firewall sitting between several internal networks. The intent of this firewall is to make traffic more secure. Given the following information perform the tasks listed below:
Untrusted zone: 0.0.0.0/0
User zone: USR 10.1.1.0/24
User zone: USR2 10.1.2.0/24
DB zone: 10.1.4.0/24
Web application zone: 10.1.5.0/24
Management zone: 10.1.10.0/24
Web server: 10.1.5.50
MS-SQL server: 10.1.4.70
MGMT platform: 10.1.10.250
Instructions: To perform the necessary tasks, please modify the DST port, SRC zone, Protocol, Action, and/or Rule Order columns. Type ANY to include all ports. Firewall ACLs are read from the top down. Once you have met the simulation requirements, click Save. When you have completed the simulation, please select the Done button to submit. Once the simulation is submitted, please select the Next button to continue.
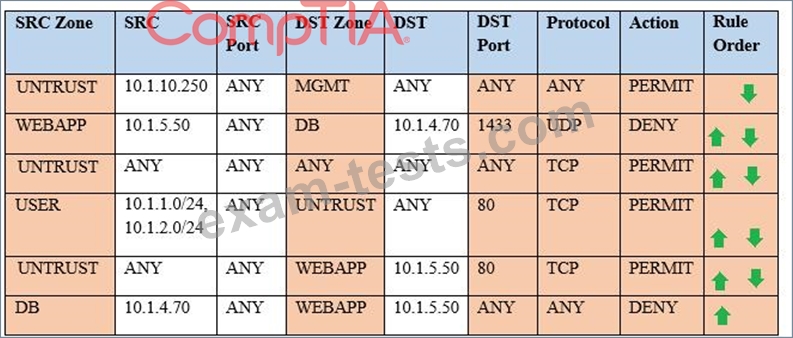
Task 1) A rule was added to prevent the management platform from accessing the internet. This rule is not working. Identify the rule and correct this issue.
Task 2) The firewall must be configured so that the SQL server can only receive requests from the web server.
Task 3) The web server must be able to receive unencrypted requests from hosts inside and outside the corporate network.
Task 4) Ensure the final rule is an explicit deny.
Task 5) Currently the user zone can access internet websites over an unencrypted protocol. Modify a rule so that user access to websites is over secure protocols only.
Instructions: To perform the necessary tasks, please modify the DST port, SRC zone, Protocol, Action, and/or Rule Order columns. Type ANY to include all ports. Firewall ACLs are read from the top down. Once you have met the simulation requirements, click Save. When you have completed the simulation, please select the Done button to submit. Once the simulation is submitted, please select the Next button to continue.
Untrusted zone: 0.0.0.0/0
User zone: USR 10.1.1.0/24
User zone: USR2 10.1.2.0/24
DB zone: 10.1.4.0/24
Web application zone: 10.1.5.0/24
Management zone: 10.1.10.0/24
Web server: 10.1.5.50
MS-SQL server: 10.1.4.70
MGMT platform: 10.1.10.250
Instructions: To perform the necessary tasks, please modify the DST port, SRC zone, Protocol, Action, and/or Rule Order columns. Type ANY to include all ports. Firewall ACLs are read from the top down. Once you have met the simulation requirements, click Save. When you have completed the simulation, please select the Done button to submit. Once the simulation is submitted, please select the Next button to continue.

Task 1) A rule was added to prevent the management platform from accessing the internet. This rule is not working. Identify the rule and correct this issue.
Task 2) The firewall must be configured so that the SQL server can only receive requests from the web server.
Task 3) The web server must be able to receive unencrypted requests from hosts inside and outside the corporate network.
Task 4) Ensure the final rule is an explicit deny.
Task 5) Currently the user zone can access internet websites over an unencrypted protocol. Modify a rule so that user access to websites is over secure protocols only.
Instructions: To perform the necessary tasks, please modify the DST port, SRC zone, Protocol, Action, and/or Rule Order columns. Type ANY to include all ports. Firewall ACLs are read from the top down. Once you have met the simulation requirements, click Save. When you have completed the simulation, please select the Done button to submit. Once the simulation is submitted, please select the Next button to continue.
Question 159
A penetration testing manager is contributing to an RFP for the purchase of a new platform. The manager has provided the following requirements:
* Must be able to MITM web-based protocols
* Must be able to find common misconfigurations and security holes
Which of the following types of testing should be included in the testing platform? (Choose two.)
* Must be able to MITM web-based protocols
* Must be able to find common misconfigurations and security holes
Which of the following types of testing should be included in the testing platform? (Choose two.)
Question 160
During a security assessment, activities were divided into two phases; internal and external exploitation.
The security assessment team set a hard time limit on external activities before moving to a compromised
box within the enterprise perimeter.
Which of the following methods is the assessment team most likely to employ NEXT?
The security assessment team set a hard time limit on external activities before moving to a compromised
box within the enterprise perimeter.
Which of the following methods is the assessment team most likely to employ NEXT?

