Question 171
In an effort to be proactive, an analyst has run an assessment against a sample workstation before auditors visit next month. The scan results are as follows:
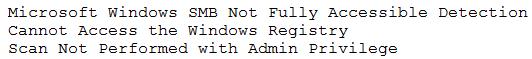
Based on the output of the scan, which of the following is the BEST answer?

Based on the output of the scan, which of the following is the BEST answer?
Question 172
A security analyst is adding input to the incident response communication plan. A company officer has suggested that if a data breach occurs, only affected parties should be notified to keep an incident from becoming a media headline. Which of the following should the analyst recommend to the company officer?
Question 173
A technician recently fixed a computer with several viruses and spyware programs on it and notices the
Internet settings were set to redirect all traffic through an unknown proxy. This type of attack is known as
which of the following?
Internet settings were set to redirect all traffic through an unknown proxy. This type of attack is known as
which of the following?
Question 174
Company A suspects an employee has been exfiltrating PII via a USB thumb drive. An analyst is tasked with attempting to locate the information on the drive. The PII in question includes the following:

Which of the following would BEST accomplish the task assigned to the analyst?

Which of the following would BEST accomplish the task assigned to the analyst?
Question 175
A Chief Executive Officer (CEO) wants to implement BYOD in the environment. Which of the following options should the security analyst suggest to protect corporate data on these devices? (Choose two.)

