Question 166
An analyst is searching a log for potential credit card leaks. The log stores all data encoded in hexadecimal. Which of the following commands will allow the security analyst to confirm the incident?
Question 167
A security analyst needs to develop a brief that will include the latest incidents and the attack phases of the incidents. The goal is to support threat intelligence and identify whether or not the incidents are linked.
Which of the following methods would be MOST appropriate to use?
Which of the following methods would be MOST appropriate to use?
Question 168
The inability to do remote updates of certificates. keys software and firmware is a security issue commonly associated with:
Question 169
A technician receives the following security alert from the firewall's automated system:
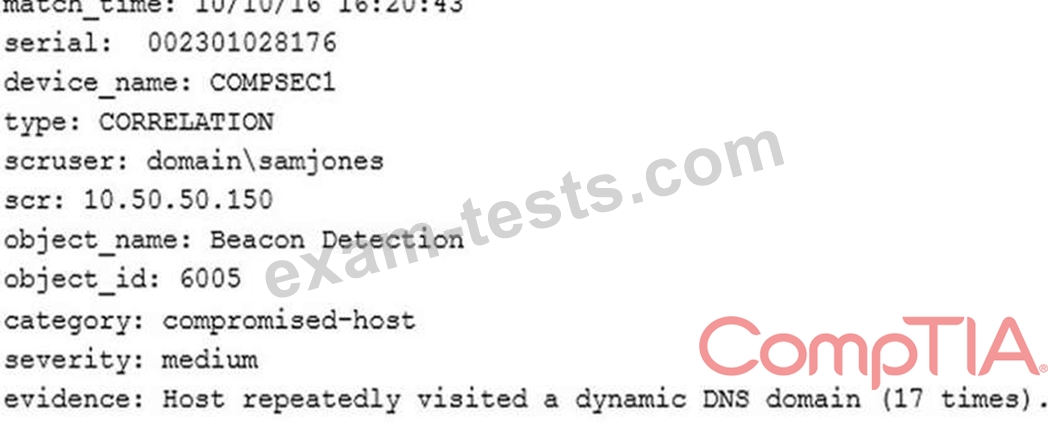
After reviewing the alert, which of the following is the BEST analysis?

After reviewing the alert, which of the following is the BEST analysis?
Question 170
A small electronics company decides to use a contractor to assist with the development of a new FPGA-based device. Several of the development phases will occur off-site at the contractor's labs.
Which of the following is the main concern a security analyst should have with this arrangement?
Which of the following is the main concern a security analyst should have with this arrangement?
Premium Bundle
Newest CS0-002 Exam PDF Dumps shared by BraindumpsPass.com for Helping Passing CS0-002 Exam! BraindumpsPass.com now offer the updated CS0-002 exam dumps, the BraindumpsPass.com CS0-002 exam questions have been updated and answers have been corrected get the latest BraindumpsPass.com CS0-002 pdf dumps with Exam Engine here:

