Question 156
The security configuration management policy states that all patches must undergo testing procedures before being moved into production. The security analyst notices a single web application server has been downloading and applying patches during non-business hours without testing. There are no apparent adverse reactions, server functionality does not seem to be affected, and no malware was found after a scan.
Which of the following actions should the analyst take?
Which of the following actions should the analyst take?
Question 157
The help desk informed a security analyst of a trend that is beginning to develop regarding a suspicious email that has been reported by multiple users.
The analyst has determined the email includes an attachment named invoice.zip that contains the following files:
Locky.js

xerty.ini

xerty.lib

Further analysis indicates that when the .zip file is opened, it is installing a new version of ransomware on the devices.
Which of the following should be done FIRST to prevent data on the company NAS from being encrypted by infected devices?
The analyst has determined the email includes an attachment named invoice.zip that contains the following files:
Locky.js

xerty.ini

xerty.lib

Further analysis indicates that when the .zip file is opened, it is installing a new version of ransomware on the devices.
Which of the following should be done FIRST to prevent data on the company NAS from being encrypted by infected devices?
Question 158
A vulnerability scan came back with critical findings for a Microsoft SharePoint server:
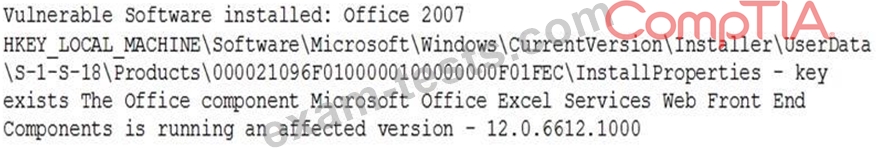
Which of the following actions should be taken?

Which of the following actions should be taken?
Question 159
An information security analyst is compiling data from a recent penetration test and reviews the following output:
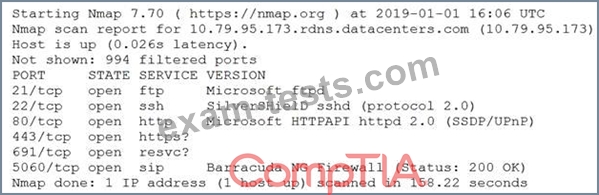
The analyst wants to obtain more information about the web-based services that are running on the target.
Which of the following commands would MOST likely provide the needed information?

The analyst wants to obtain more information about the web-based services that are running on the target.
Which of the following commands would MOST likely provide the needed information?
Question 160
A security professional is analyzing the results of a network utilization report. The report includes the following information:
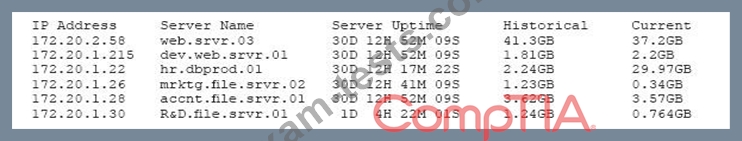
Which of the following servers needs further investigation?

Which of the following servers needs further investigation?

