Question 171
A new on-premises application server was recently installed on the network. Remote access to the server was enabled for vendor support on required ports, but recent security reports show large amounts of data are being sent to various unauthorized networks through those ports. Which of the following configuration changes must be implemented to resolve this security issue while still allowing remote vendor access?
Question 172
A bad actor bypasses authentication and reveals all records in a database through an SQL injection. Implementation of which of the following would work BEST to prevent similar attacks in
Question 173
During the forensic a phase of security investigation, it was discovered that an attacker was able to find private keys on a poorly secured team shared drive. The attacker used those keys to intercept and decrypt sensitive traffic on a web server. Which of the following describes this type of exploit and the potential remediation?
Question 174
A security analyst is creating baseline system images to remediate vulnerabilities found in different operating systems. Each image needs to be scanned before it is deployed.
The security analyst must ensure the configurations match industry standard benchmarks and the process can be repeated frequently.
Which of the following vulnerability options would BEST create the process requirements?
The security analyst must ensure the configurations match industry standard benchmarks and the process can be repeated frequently.
Which of the following vulnerability options would BEST create the process requirements?
Question 175
The help desk noticed a security analyst that emails from a new email server are not being sent out. The new email server was recently to the existing ones. The analyst runs the following command on the new server.
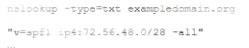
Given the output, which of the following should the security analyst check NEXT?
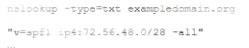
Given the output, which of the following should the security analyst check NEXT?

