Question 141
Which of the following countermeasures should the security administrator apply to MOST effectively mitigate Bootkit-level infections of the organization's workstation devices?
Question 142
A SIEM alert occurs with the following output:
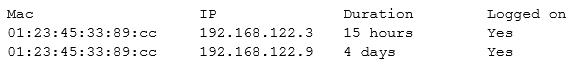
Which of the following BEST describes this alert?

Which of the following BEST describes this alert?
Question 143
An analyst performs a routine scan of a host using Nmap and receives the following output:
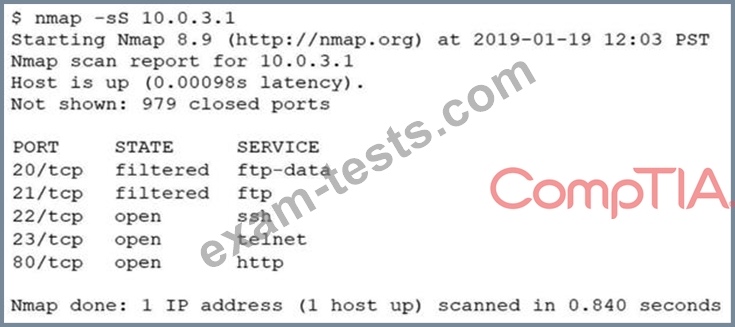
Which of the following should the analyst investigate FIRST?

Which of the following should the analyst investigate FIRST?
Question 144
A security analyst suspects a malware infection was caused by a user who downloaded malware after clicking
http://<malwaresource>/a.php in a phishing email.
To prevent other computers from being infected by the same malware variation, the analyst should create a rule on the.
http://<malwaresource>/a.php in a phishing email.
To prevent other computers from being infected by the same malware variation, the analyst should create a rule on the.
Question 145
Which of the following policies BEST explains the purpose of a data ownership policy?

