Question 191
Due to new regulations, a company has decided to institute an organizational vulnerability management program and assign the function to the security team.
Which of the following frameworks would BEST support the program? (Select two.)
Which of the following frameworks would BEST support the program? (Select two.)
Question 192
An analyst was testing the latest version of an internally developed CRM system. The analyst created a basic user account. Using a few tools in Kali's latest distribution, the analyst was able to access configuration files, change permissions on folders and groups, and delete and create new system objects. Which of the following techniques did the analyst use to perform these unauthorized activities?
Question 193
For machine learning to be applied effectively toward security analysis automation, it requires.
Question 194
In an effort to be proactive, an analyst has run an assessment against a sample workstation before auditors visit next month. The scan results are as follows:
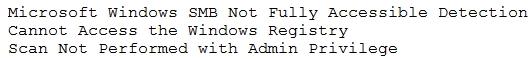
Based on the output of the scan, which of the following is the BEST answer?

Based on the output of the scan, which of the following is the BEST answer?
Question 195
A security analyst is reviewing vulnerability scan results and notices new workstations are being flagged as having outdated antivirus signatures. The analyst observes the following plugin output:

The analyst uses the vendor's website to confirm the oldest supported version is correct. Which of the following BEST describes the situation?

The analyst uses the vendor's website to confirm the oldest supported version is correct. Which of the following BEST describes the situation?
Premium Bundle
Newest CS0-002 Exam PDF Dumps shared by BraindumpsPass.com for Helping Passing CS0-002 Exam! BraindumpsPass.com now offer the updated CS0-002 exam dumps, the BraindumpsPass.com CS0-002 exam questions have been updated and answers have been corrected get the latest BraindumpsPass.com CS0-002 pdf dumps with Exam Engine here:

