Question 186
A security analyst recently discovered two unauthorized hosts on the campus's wireless network segment from a man-m-the-middle attack.
The security analyst also verified that privileges were not escalated, and the two devices did not gain access to other network devices.
Which of the following would BEST mitigate and improve the security posture of the wireless network for this type of attack?
The security analyst also verified that privileges were not escalated, and the two devices did not gain access to other network devices.
Which of the following would BEST mitigate and improve the security posture of the wireless network for this type of attack?
Question 187
Which of the following BEST describes the offensive participants in a tabletop exercise?
Question 188
The Chief Information Security Officer (CISO) has asked the security analyst to examine abnormally high processor utilization on a key server. The output below is from the company's research and development (R&D) server.
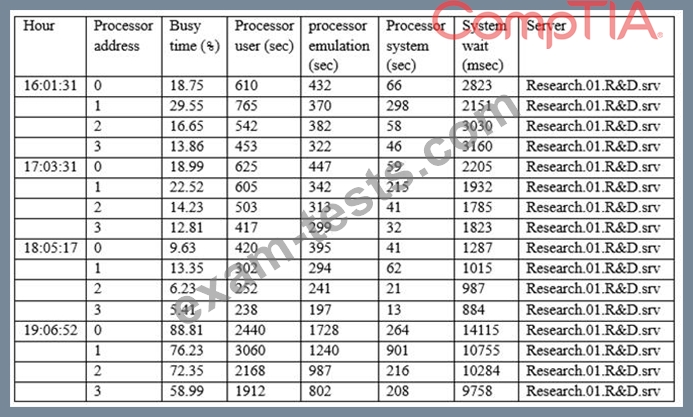
Which of the following actions should the security analyst take FIRST?

Which of the following actions should the security analyst take FIRST?
Question 189
During an investigation, a security analyst determines suspicious activity occurred during the night shift over the weekend. Further investigation reveals the activity was initiated from an internal IP going to an external website.
Which of the following would be the MOST appropriate recommendation to prevent the activity from happening in the future?
Which of the following would be the MOST appropriate recommendation to prevent the activity from happening in the future?
Question 190
The following IDS log was discovered by a company's cybersecurity analyst:

Which of the following was launched against the company based on the IDS log?

Which of the following was launched against the company based on the IDS log?

