Question 181
A vulnerability scan returned the following results for a web server that hosts multiple wiki sites:
Apache-HTTPD-cve-2014-023: Apache HTTPD: mod_cgid denial of service CVE-2014- Due to a flaw found in mog_cgid, a server using mod_cgid to host CGI scripts could be vulnerable to a DoS attack caused by a remote attacker who is exploiting a weakness in non-standard input, causing processes to hang indefinitely.
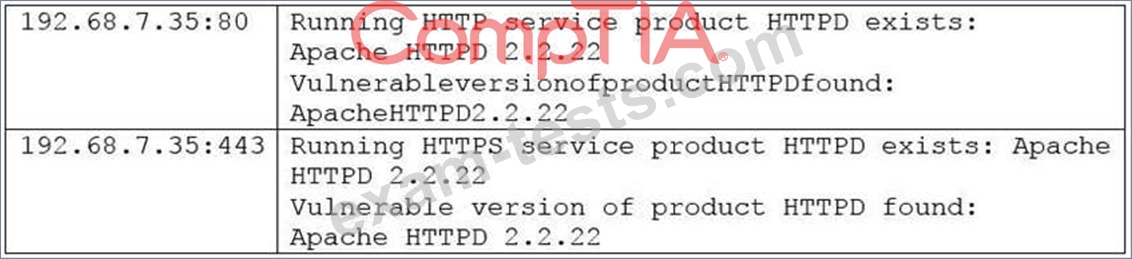
The security analyst has confirmed the server hosts standard CGI scripts for the wiki sites, does not have mod_cgid installed, is running Apache 2.2.22, and is not behind a WAF. The server is located in the DMZ, and the purpose of the server is to allow customers to add entries into a publicly accessible database.
Which of the following would be the MOST efficient way to address this finding?
Apache-HTTPD-cve-2014-023: Apache HTTPD: mod_cgid denial of service CVE-2014- Due to a flaw found in mog_cgid, a server using mod_cgid to host CGI scripts could be vulnerable to a DoS attack caused by a remote attacker who is exploiting a weakness in non-standard input, causing processes to hang indefinitely.

The security analyst has confirmed the server hosts standard CGI scripts for the wiki sites, does not have mod_cgid installed, is running Apache 2.2.22, and is not behind a WAF. The server is located in the DMZ, and the purpose of the server is to allow customers to add entries into a publicly accessible database.
Which of the following would be the MOST efficient way to address this finding?
Question 182
A security analyst has received information from a third-party intelligence-sharing resource that indicates employee accounts were breached.
Which of the following is the NEXT step the analyst should take to address the issue?
Which of the following is the NEXT step the analyst should take to address the issue?
Question 183
A cybersecurity analyst is currently checking a newly deployed server that has an access control list applied. When conducting the scan, the analyst received the following code snippet of results:
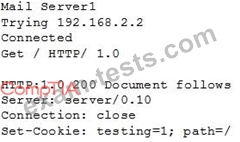
Which of the following describes the output of this scan?

Which of the following describes the output of this scan?
Question 184
In web application scanning, static analysis refers to scanning:
Question 185
In order to meet regulatory compliance objectives for the storage of PHI, vulnerability scans must be conducted on a continuous basis.
The last completed scan of the network returned 5,682 possible vulnerabilities.
The Chief Information Officer (CIO) would like to establish a remediation plan to resolve all known issues.
Which of the following is the BEST way to proceed?
The last completed scan of the network returned 5,682 possible vulnerabilities.
The Chief Information Officer (CIO) would like to establish a remediation plan to resolve all known issues.
Which of the following is the BEST way to proceed?
Premium Bundle
Newest CS0-002 Exam PDF Dumps shared by BraindumpsPass.com for Helping Passing CS0-002 Exam! BraindumpsPass.com now offer the updated CS0-002 exam dumps, the BraindumpsPass.com CS0-002 exam questions have been updated and answers have been corrected get the latest BraindumpsPass.com CS0-002 pdf dumps with Exam Engine here:

