Question 196
A hacker issued a command and received the following response:
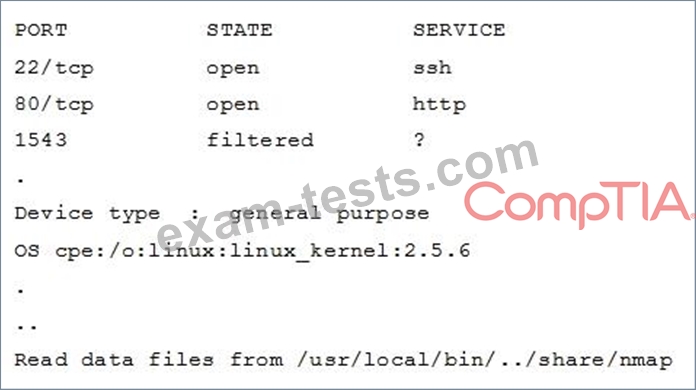
Which of the following describes what the hacker is attempting?

Which of the following describes what the hacker is attempting?
Question 197
A security analyst is reviewing packet captures from a system that was compromised. The system was already isolated from the network, but it did have network access for a few hours after being compromised. When viewing the capture in a packet analyzer, the analyst sees the following:

Which of the following can the analyst conclude?

Which of the following can the analyst conclude?
Question 198
While reviewing web server logs, a security analyst notices the following code:
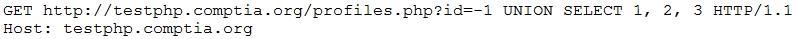
Which of the following would prevent this code from performing malicious actions?
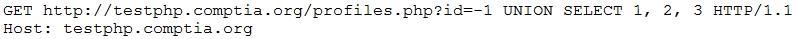
Which of the following would prevent this code from performing malicious actions?
Question 199
A cybersecurity analyst is investigating a potential incident affecting multiple systems on a company's internal network. Although there is a negligible impact to performance, the following symptom present on each of the affected systems:
* Existence of a new and unexpected svchost exe process
* Persistent, outbound TCP/IP connections to an unknown external host with routine keep-alives transferred
* DNS query logs showing successful name resolution for an Internet-resident dynamic DNS domain If this situation remains unresolved, which of the following will MOST likely occur?
* Existence of a new and unexpected svchost exe process
* Persistent, outbound TCP/IP connections to an unknown external host with routine keep-alives transferred
* DNS query logs showing successful name resolution for an Internet-resident dynamic DNS domain If this situation remains unresolved, which of the following will MOST likely occur?
Question 200
While planning segmentation for an ICS environment, a security engineer determines IT resources will need access to devices within the ICS environment without compromising security.
To provide the MOST secure access model in this scenario, the jumpbox should be.
To provide the MOST secure access model in this scenario, the jumpbox should be.
Premium Bundle
Newest CS0-002 Exam PDF Dumps shared by BraindumpsPass.com for Helping Passing CS0-002 Exam! BraindumpsPass.com now offer the updated CS0-002 exam dumps, the BraindumpsPass.com CS0-002 exam questions have been updated and answers have been corrected get the latest BraindumpsPass.com CS0-002 pdf dumps with Exam Engine here:

