Question 201
A cybersecurity analyst was asked to discover the hardware address of 30 networked assets.
From a command line, which of the following tools would be used to provide ARP scanning and reflects the MOST efficient method for accomplishing the task?
From a command line, which of the following tools would be used to provide ARP scanning and reflects the MOST efficient method for accomplishing the task?
Question 202
A security analyst on the threat-hunting team has developed a list of unneeded, benign services that are currently running as part of the standard OS deployment for workstations. The analyst will provide this list to the operations team to create a policy that will automatically disable the services for all workstations in the organization.
Which of the following BEST describes the security analyst's goal?
Which of the following BEST describes the security analyst's goal?
Question 203
A security analyst has discovered trial developers have installed browsers on all development servers in the company's cloud infrastructure and are using them to browse the Internet. Which of the following changes should the security analyst make to BEST protect the environment?
Question 204
A cybersecurity analyst is hired to review the security measures implemented within the domain controllers of a company. Upon review, the cybersecurity analyst notices a brute force attack can be launched against domain controllers that run on a Windows platform. The first remediation step implemented by the cybersecurity analyst is to make the account passwords more complex.
Which of the following is the NEXT remediation step the cybersecurity analyst needs to implement?
Which of the following is the NEXT remediation step the cybersecurity analyst needs to implement?
Question 205
A security analyst is preparing for the company's upcoming audit. Upon review of the company's latest vulnerability scan, the security analyst finds the following open issues:
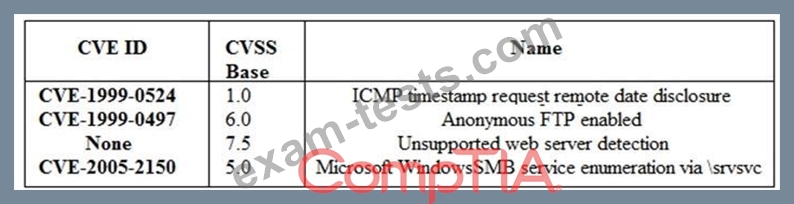
Which of the following vulnerabilities should be prioritized for remediation FIRST?

Which of the following vulnerabilities should be prioritized for remediation FIRST?

