Question 206
Which of the following is a technology used to provide Internet access to internal associates without exposing the Internet directly to the associates?
Question 207
A security analyst for a large financial institution is creating a threat model for a specific threat actor that is likely targeting an organization's financial assets.
Which of the following is the BEST example of the level of sophistication this threat actor is using?
Which of the following is the BEST example of the level of sophistication this threat actor is using?
Question 208
A security analyst is reviewing packet captures to determine the extent of success during an attacker's reconnaissance phase following a recent incident.
The following is a hex and ASCII dump of one such packet:

Which of the following BEST describes this packet?
The following is a hex and ASCII dump of one such packet:

Which of the following BEST describes this packet?
Question 209
A company creates digitally signed packages for its devices. Which of the following BEST describes the method by which the security packages are delivered to the company's customers?
Question 210
A company's IDP/DLP solution triggered the following alerts:
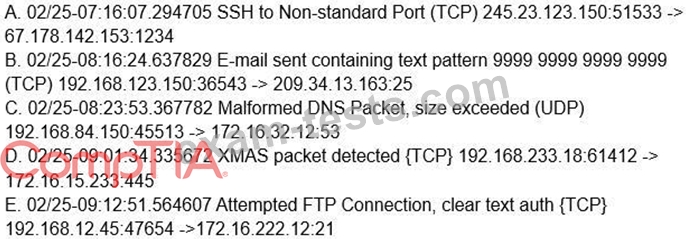
Which of the following alerts should a security analyst investigate FIRST?

Which of the following alerts should a security analyst investigate FIRST?
Premium Bundle
Newest CS0-002 Exam PDF Dumps shared by BraindumpsPass.com for Helping Passing CS0-002 Exam! BraindumpsPass.com now offer the updated CS0-002 exam dumps, the BraindumpsPass.com CS0-002 exam questions have been updated and answers have been corrected get the latest BraindumpsPass.com CS0-002 pdf dumps with Exam Engine here:

