Question 31
An employee is suspected of misusing a company-issued laptop. The employee has been suspended pending an investigation by human resources. Which of the following is the best step to preserve evidence?
Question 32
A security administrator has been notified by the IT operations department that some vulnerability reports contain an incomplete list of findings. Which of the following methods should be used to resolve this issue?
Question 33
A zero-day command injection vulnerability was published. A security administrator is analyzing the following logs for evidence of adversaries attempting to exploit the vulnerability:
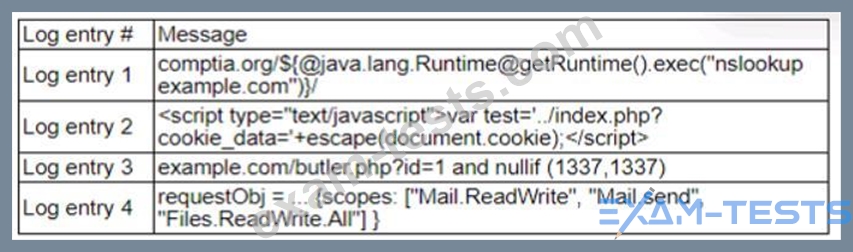
Which of the following log entries provides evidence of the attempted exploit?

Which of the following log entries provides evidence of the attempted exploit?
Question 34
Which of the following is the most important factor to ensure accurate incident response reporting?
Question 35
A technician is analyzing output from a popular network mapping tool for a PCI audit:
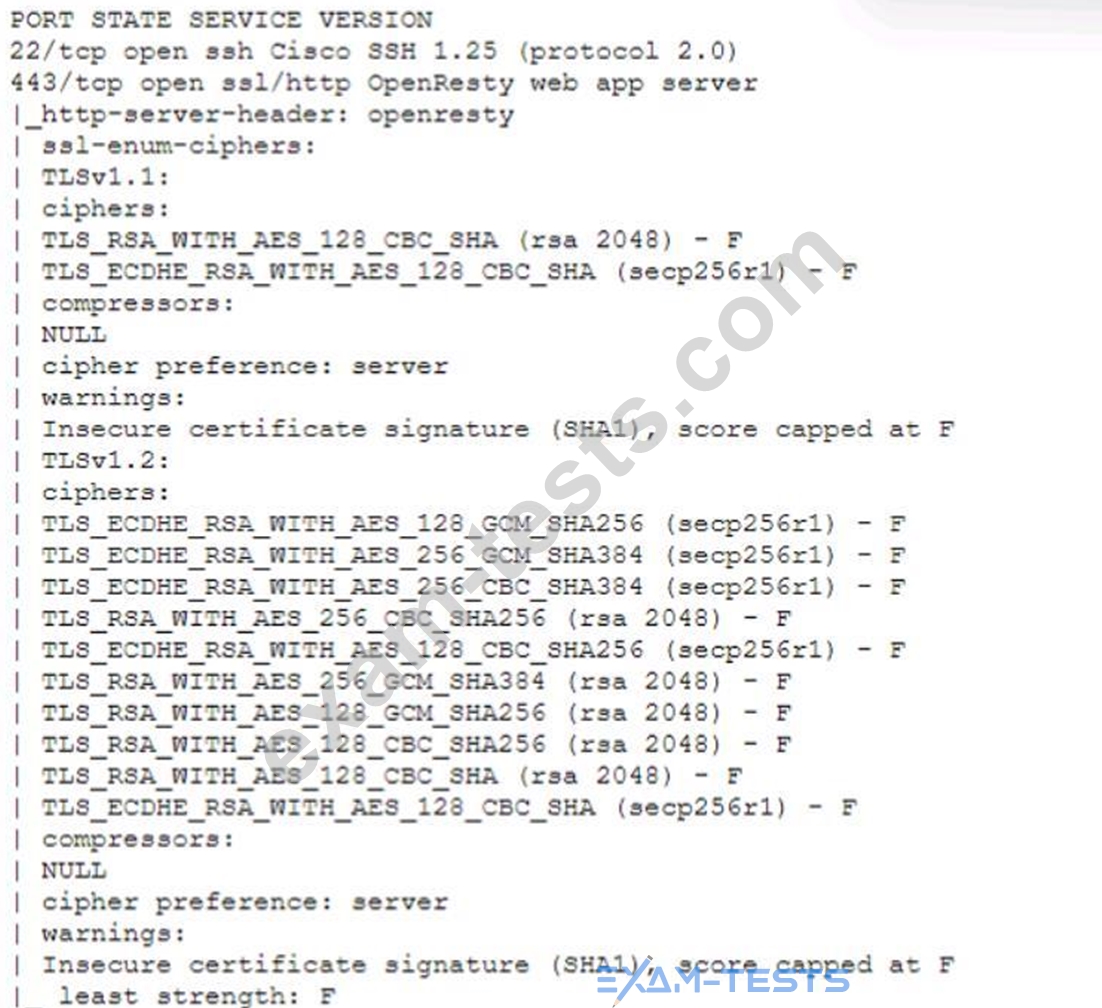
Which of the following best describes the output?

Which of the following best describes the output?

