Question 21
A systems analyst is limiting user access to system configuration keys and values in a Windows environment.
Which of the following describes where the analyst can find these configuration items?
Which of the following describes where the analyst can find these configuration items?
Question 22
An incident response team receives an alert to start an investigation of an internet outage. The outage is preventing all users in multiple locations from accessing external SaaS resources. The team determines the organization was impacted by a DDoS attack. Which of the following logs should the team review first?
Question 23
Which of the following is the best metric for an organization to focus on given recent investments in SIEM, SOAR, and a ticketing system?
Question 24
Approximately 100 employees at your company have received a Phishing email. AS a security analyst. you have been tasked with handling this Situation.
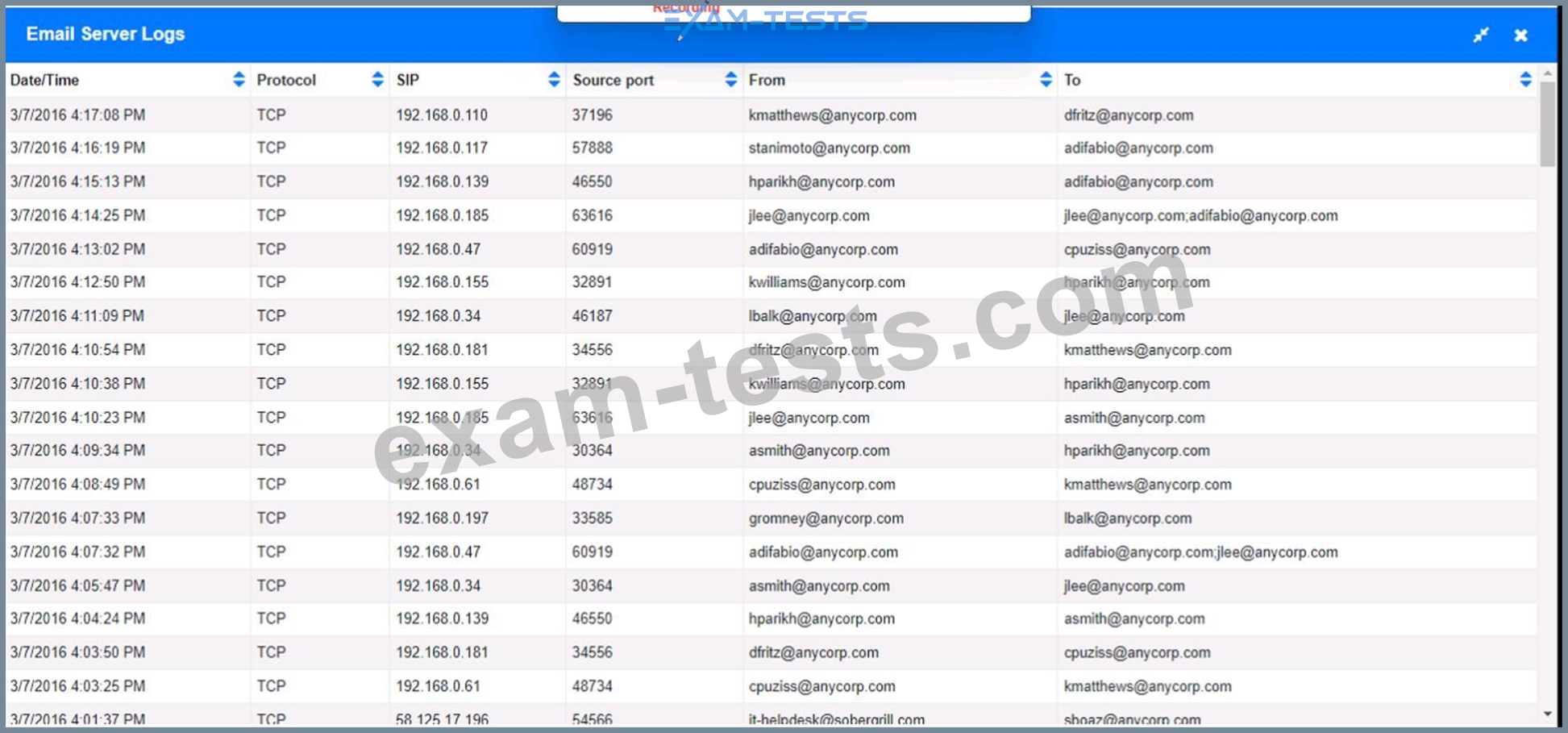
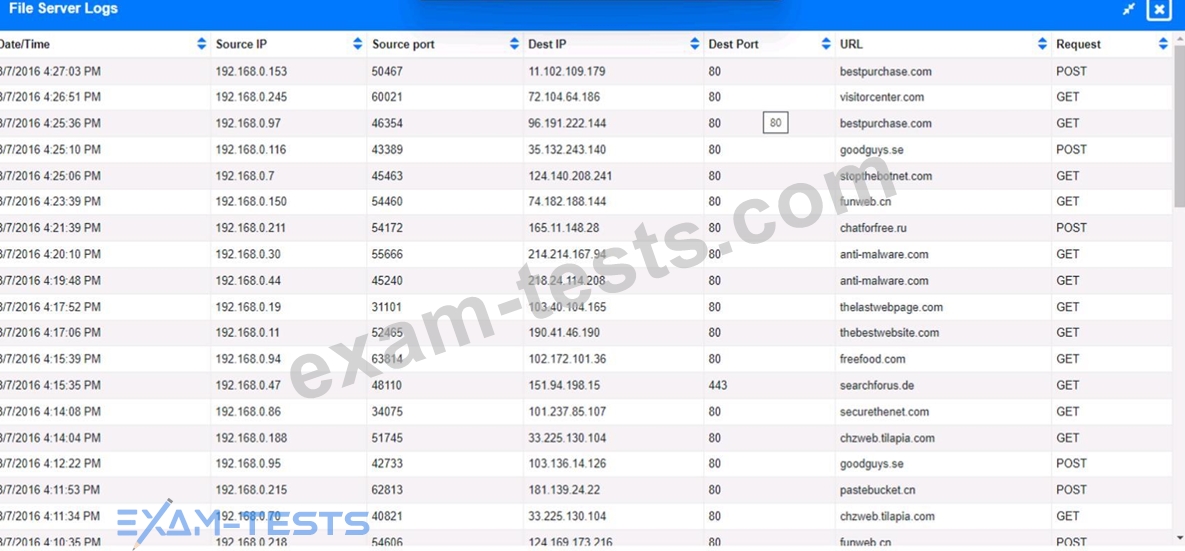
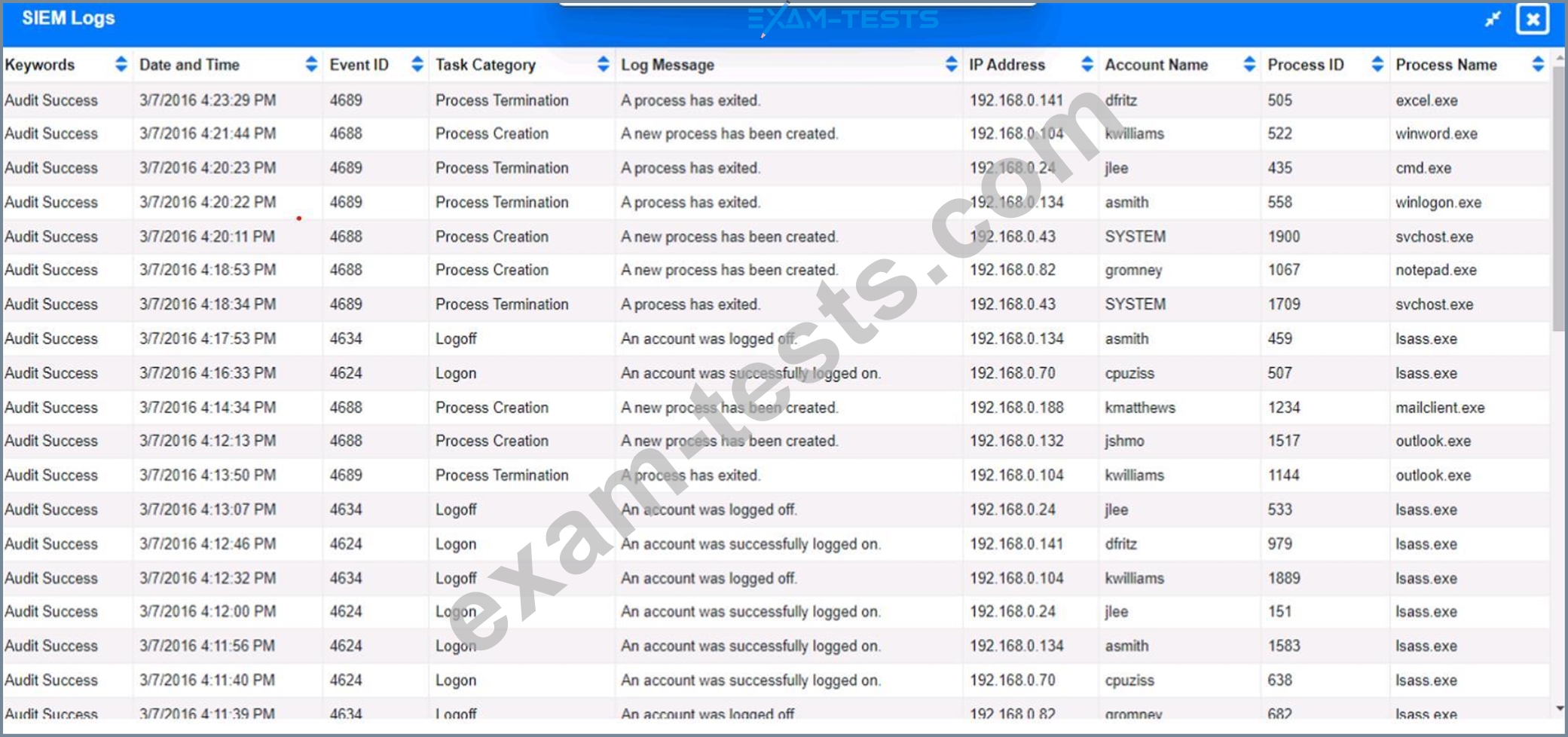
Review the information provided and determine the following:
1. HOW many employees Clicked on the link in the Phishing email?
2. on how many workstations was the malware installed?
3. what is the executable file name of the malware?
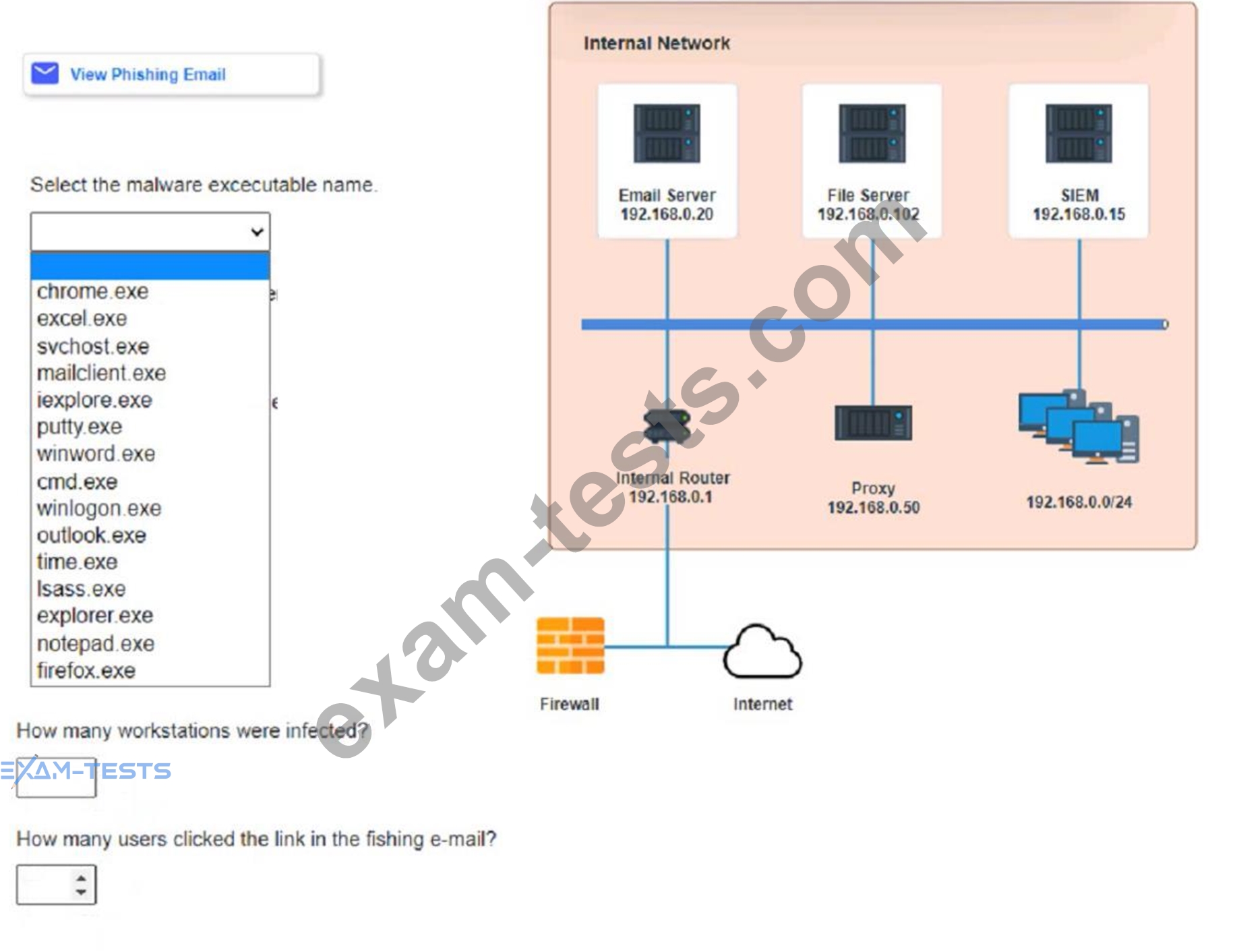



Review the information provided and determine the following:
1. HOW many employees Clicked on the link in the Phishing email?
2. on how many workstations was the malware installed?
3. what is the executable file name of the malware?

Question 25
The security operations team is required to consolidate several threat intelligence feeds due to redundant tools and portals. Which of the following will best achieve the goal and maximize results?

