Question 16
Which of the following security operations tasks are ideal for automation?
Question 17
A security analyst receives an alert for suspicious activity on a company laptop An excerpt of the log is shown below:
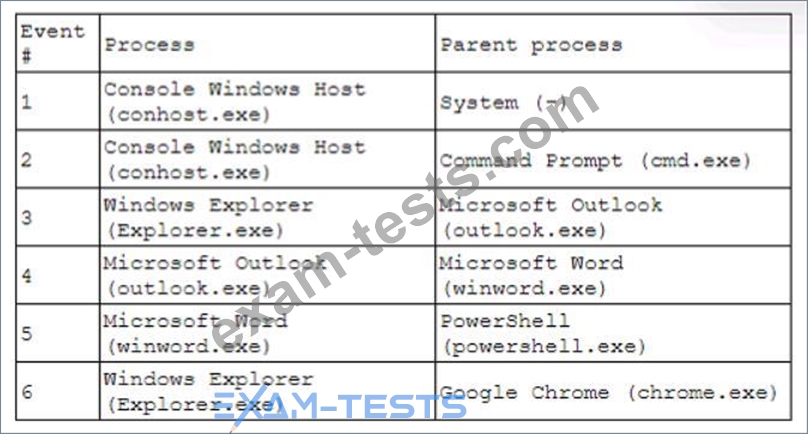
Which of the following has most likely occurred?

Which of the following has most likely occurred?
Question 18
An analyst notices there is an internal device sending HTTPS traffic with additional characters in the header to a known-malicious IP in another country. Which of the following describes what the analyst has noticed?
Question 19
A security program was able to achieve a 30% improvement in MTTR by integrating security controls into a SIEM. The analyst no longer had to jump between tools. Which of the following best describes what the security program did?
Question 20
A recent penetration test discovered that several employees were enticed to assist attackers by visiting specific websites and running downloaded files when prompted by phone calls. Which of the following would best address this issue?

