Question 11
While reviewing web server logs, an analyst notices several entries with the same time stamps, but all contain odd characters in the request line. Which of the following steps should be taken next?
Question 12
An incident response team is working with law enforcement to investigate an active web server compromise.
The decision has been made to keep the server running and to implement compensating controls for a period of time. The web service must be accessible from the internet via the reverse proxy and must connect to a database server. Which of the following compensating controls will help contain the adversary while meeting the other requirements? (Select two).
The decision has been made to keep the server running and to implement compensating controls for a period of time. The web service must be accessible from the internet via the reverse proxy and must connect to a database server. Which of the following compensating controls will help contain the adversary while meeting the other requirements? (Select two).
Question 13
Which of the following concepts is using an API to insert bulk access requests from a file into an identity management system an example of?
Question 14
The security team reviews a web server for XSS and runs the following Nmap scan:

Which of the following most accurately describes the result of the scan?

Which of the following most accurately describes the result of the scan?
Question 15
An organization conducted a web application vulnerability assessment against the corporate website, and the following output was observed:
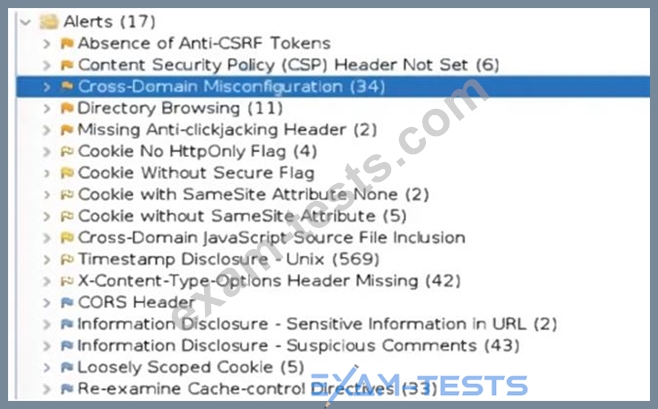
Which of the following tuning recommendations should the security analyst share?

Which of the following tuning recommendations should the security analyst share?

