Question 151
A security analyst is reviewing events that occurred during a possible compromise. The analyst obtains the following log:
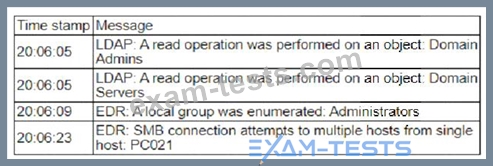
Which of the following is most likely occurring, based on the events in the log?

Which of the following is most likely occurring, based on the events in the log?
Question 152
A security analyst has prepared a vulnerability scan that contains all of the company's functional subnets. During the initial scan, users reported that network printers began to print pages that contained unreadable text and icons.
Which of the following should the analyst do to ensure this behavior does not oocur during subsequent vulnerability scans?
Which of the following should the analyst do to ensure this behavior does not oocur during subsequent vulnerability scans?
Question 153
An incident response analyst is investigating the root cause of a recent malware outbreak. Initial binary analysis indicates that this malware disables host security services and performs cleanup routines on its infected hosts, including deletion of initial dropper and removal of event log entries and prefetch files from the host. Which of the following data sources would most likely reveal evidence of the root cause? (Choose two.)
Question 154
An organization has established a formal change management process after experiencing several critical system failures over the past year. Which of the following are key factors that the change management process will include in order to reduce the impact of system failures?
(Choose two.)
(Choose two.)
Question 155
A company has decided to expose several systems to the internet, The systems are currently available internally only. A security analyst is using a subset of CVSS3.1 exploitability metrics to prioritize the vulnerabilities that would be the most exploitable when the systems are exposed to the internet. The systems and the vulnerabilities are shown below:
Which of the following systems should be prioritized for patching?
Which of the following systems should be prioritized for patching?

