Question 161
An organization was compromised, and the usernames and passwords of all em-ployees were leaked online.
Which of the following best describes the remedia-tion that could reduce the impact of this situation?
Which of the following best describes the remedia-tion that could reduce the impact of this situation?
Question 162
Before adopting a disaster recovery plan, some team members need to gather in a room to review the written scenarios. Which of the following best describes what the team is doing?
Question 163
The Chief Information Security Officer (CISO) of a large management firm has selected a cybersecurity framework that will help the organization demonstrate its investment in tools and systems to protect its data. Which of the following did the CISO most likely select?
Question 164
The security team at a company, which was a recent target of ransomware, compiled a list of hosts that were identified as impacted and in scope for this incident. Based on the following host list:
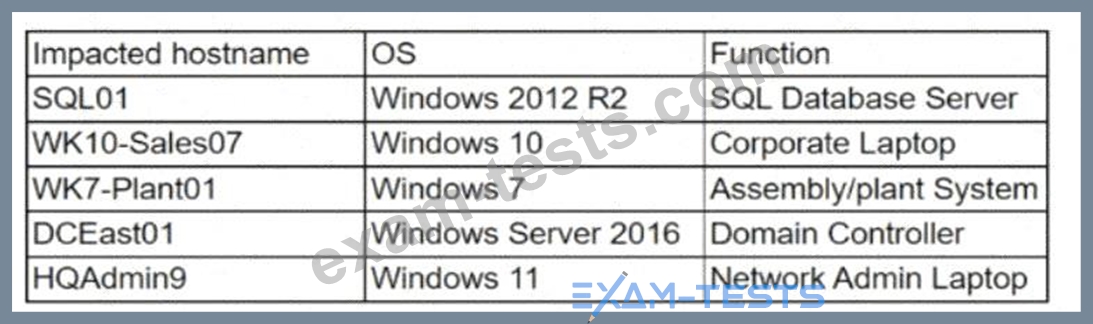
Which of the following systems was most pivotal to the threat actor in its distribution of the encryption binary via Group Policy?

Which of the following systems was most pivotal to the threat actor in its distribution of the encryption binary via Group Policy?
Question 165
A technician working at company.com received the following email:

After looking at the above communication, which of the following should the technician recommend to the security team to prevent exposure of sensitive information and reduce the risk of corporate data being stored on non-corporate assets?

After looking at the above communication, which of the following should the technician recommend to the security team to prevent exposure of sensitive information and reduce the risk of corporate data being stored on non-corporate assets?

