Question 131
During an internal code review, software called "ACE" was discovered to have a vulnerability that allows the execution of arbitrary code. The vulnerability is in a legacy, third-party vendor resource that is used by the ACE software. ACE is used worldwide and is essential for many businesses in this industry. Developers informed the Chief Information Security Officer that removal of the vulnerability will take time. Which of the following is the first action to take?
Question 132
The security analyst received the monthly vulnerability report. The following findings were included in the report
* Five of the systems only required a reboot to finalize the patch application.
* Two of the servers are running outdated operating systems and cannot be patched The analyst determines that the only way to ensure these servers cannot be compromised is to isolate them. Which of the following approaches will best minimize the risk of the outdated servers being compromised?
* Five of the systems only required a reboot to finalize the patch application.
* Two of the servers are running outdated operating systems and cannot be patched The analyst determines that the only way to ensure these servers cannot be compromised is to isolate them. Which of the following approaches will best minimize the risk of the outdated servers being compromised?
Question 133
Which of the following is the best way to begin preparation for a report titled "What We Learned" regarding a recent incident involving a cybersecurity breach?
Question 134
A vulnerability management team found four major vulnerabilities during an assessment and needs to provide a report for the proper prioritization for further mitigation. Which of the following vulnerabilities should have the highest priority for the mitigation process?
Question 135
An organization has the following risk mitigation policies:
- Risks without compensating controls will be mitigated first it the risk value is greater than
$50,000.
- Other risk mitigation will be prioritized based on risk value.
The following risks have been identified:
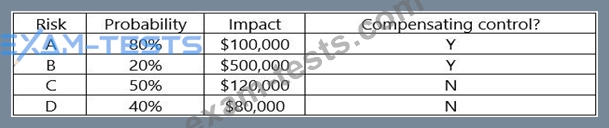
Which of the following is the order of priority for risk mitigation from highest to lowest?
- Risks without compensating controls will be mitigated first it the risk value is greater than
$50,000.
- Other risk mitigation will be prioritized based on risk value.
The following risks have been identified:

Which of the following is the order of priority for risk mitigation from highest to lowest?

