Question 171
Which of the following is the most likely reason for an organization to assign different internal departmental groups during the post-incident analysis and improvement process?
Question 172
A security audit for unsecured network services was conducted, and the following output was generated:
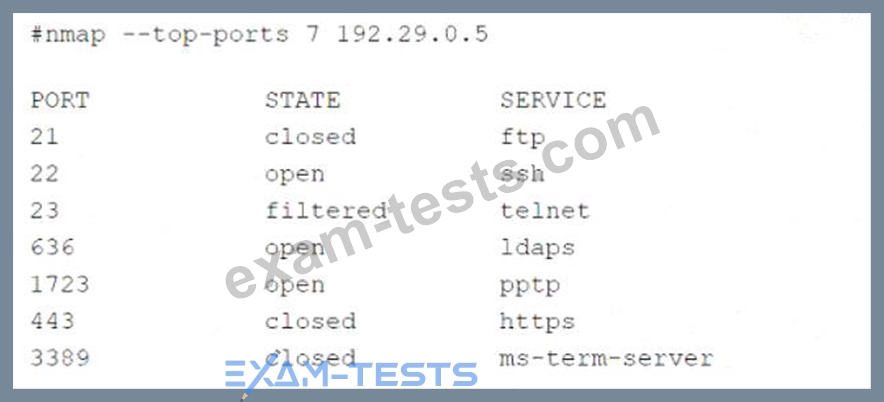
Which of the following services should the security team investigate further? (Select two).

Which of the following services should the security team investigate further? (Select two).
Question 173
Which of the following is described as a method of enforcing a security policy between cloud customers and cloud services?
Question 174
A company has a primary control in place to restrict access to a sensitive database. However, the company discovered an authentication vulnerability that could bypass this control. Which of the following is the best compensating control?
Question 175
A web application team notifies a SOC analyst that there are thousands of HTTP/404 events on the public-facing web server. Which of the following is the next step for the analyst to take?

