Question 176
Which of the following is the best way to provide realistic training for SOC analysts?
Question 177
An analyst receives alerts that state the following traffic was identified on the perimeter network firewall:
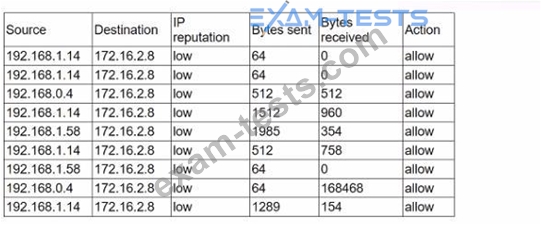
Which of the following best describes the indicator of compromise that triggered the alerts?

Which of the following best describes the indicator of compromise that triggered the alerts?
Question 178
An analyst is remediating items associated with a recent incident. The analyst has isolated the vulnerability and is actively removing it from the system. Which of the following steps of the process does this describe?
Question 179
Which of the following techniques can help a SOC team to reduce the number of alerts related to the internal security activities that the analysts have to triage?
Question 180
Company A is in the process of merging with Company B. As part of the merger, connectivity between the ERP systems must be established so pertinent financial information can be shared between the two entities. Which of the following will establish a more automated approach to secure data transfers between the two entities?

