Question 181
While a security analyst for an organization was reviewing logs from web servers. the analyst found several successful attempts to downgrade HTTPS sessions to use cipher modes of operation susceptible to padding oracle attacks. Which of the following combinations of configuration changes should the organization make to remediate this issue? (Choose two.)
Question 182
Which of the following actions would an analyst most likely perform after an incident has been investigated?
Question 183
Which of the following should be updated after a lessons-learned review?
Question 184
A penetration tester is conducting a test on an organization's software development website. The penetration tester sends the following request to the web interface:
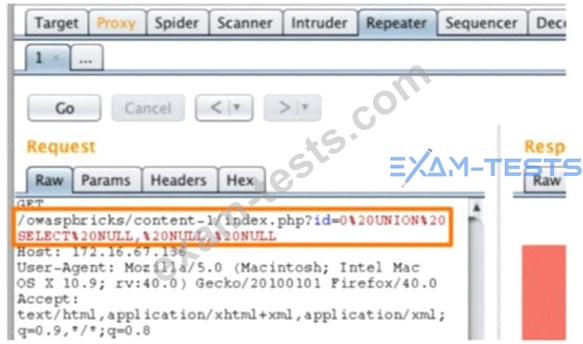
Which of the following exploits is most likely being attempted?

Which of the following exploits is most likely being attempted?
Question 185
An incident response analyst is investigating the root cause of a recent malware outbreak. Initial binary analysis indicates that this malware disables host security services and performs cleanup routines on it infected hosts, including deletion of initial dropper and removal of event log entries and prefetch files from the host.
Which of the following data sources would most likely reveal evidence of the root cause?
(Select two).
Which of the following data sources would most likely reveal evidence of the root cause?
(Select two).

