Question 206
An employee received a phishing email that contained malware targeting the company. Which of the following is the best way for a security analyst to get more details about the malware and avoid disclosing information?
Question 207
Due to reports of unauthorized activity that was occurring on the internal network, an analyst is performing a network discovery. The analyst runs an Nmap scan against a corporate network to evaluate which devices were operating in the environment. Given the following output:
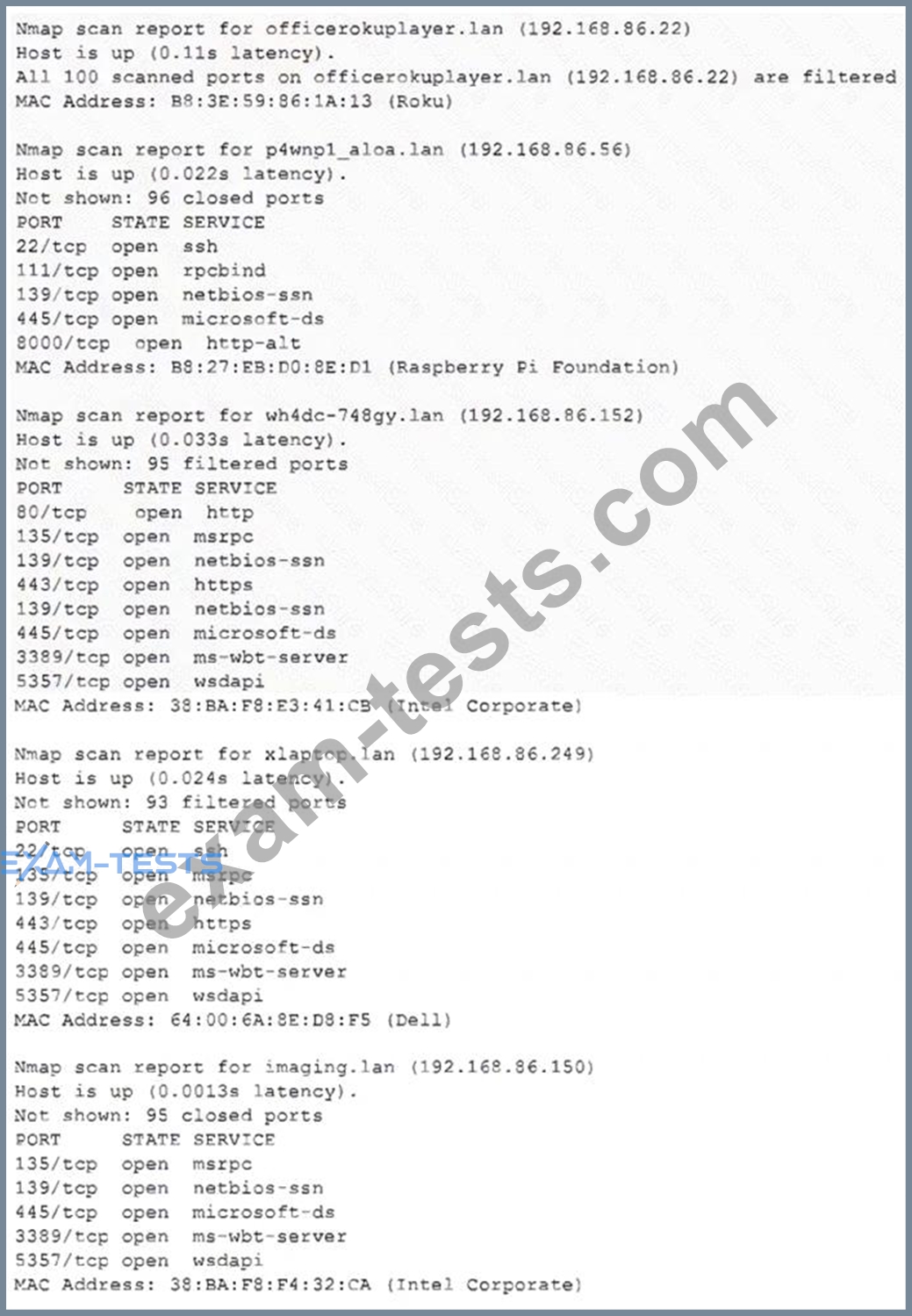
Which of the following choices should the analyst look at first?

Which of the following choices should the analyst look at first?
Question 208
A software developer is correcting the error-handling capabilities of an application following the initial coding of the fix.
Which of the following would the software developer MOST likely performed to validate the code poor to pushing it to production?
Which of the following would the software developer MOST likely performed to validate the code poor to pushing it to production?
Question 209
After updating the email client to the latest patch, only about 15% of the workforce is able to use email. Windows 10 users do not experience issues, but Windows 11 users have constant issues.
Which of the following did the change management team fail to do?
Which of the following did the change management team fail to do?
Question 210
The Chief Executive Officer of an organization recently heard that exploitation of new attacks in the industry was happening approximately 45 days after a patch was released.
Which of the following would best protect this organization?
Which of the following would best protect this organization?

