Question 6
A penetration tester has access to a local machine running Linux, but the account has limited privileges. Which of the following types of files could the tester BEST use for privilege escalation?
Question 7
A security consultant is trying to attack a device with a previously identified user account.
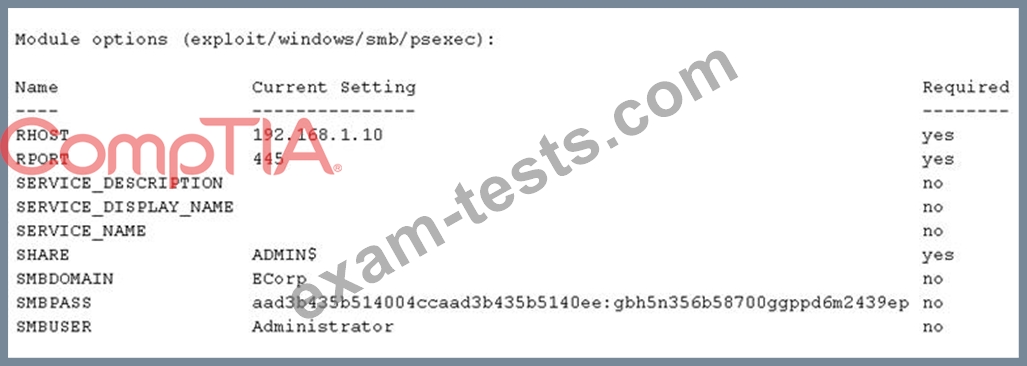
Which of the following types of attacks is being executed?

Which of the following types of attacks is being executed?
Question 8
During testing, a critical vulnerability is discovered on a client's core server. Which of the following should be the NEXT action?
Question 9
A penetration tester successfully exploits a Windows host and dumps the hashes Which of the following hashes can the penetration tester use to perform a pass-the-hash attack?
A)

B)

C)

D)

A)

B)

C)

D)

Question 10
A security assessor is attempting to craft specialized XML files to test the security of the parsing functions during ingest into a Windows application.
Before beginning to test the application, which of the following should the assessor request from the organization?
Before beginning to test the application, which of the following should the assessor request from the organization?

