Question 96
A computer on a company network was infected with a zero-day exploit after an employee accidently opened an email that contained malicious content. The employee recognized the email as malicious and was attempting to delete it, but accidently opened it.
Which of the following should be done to prevent this scenario from occurring again in the future?
Which of the following should be done to prevent this scenario from occurring again in the future?
Question 97
An attack has occurred against a company.
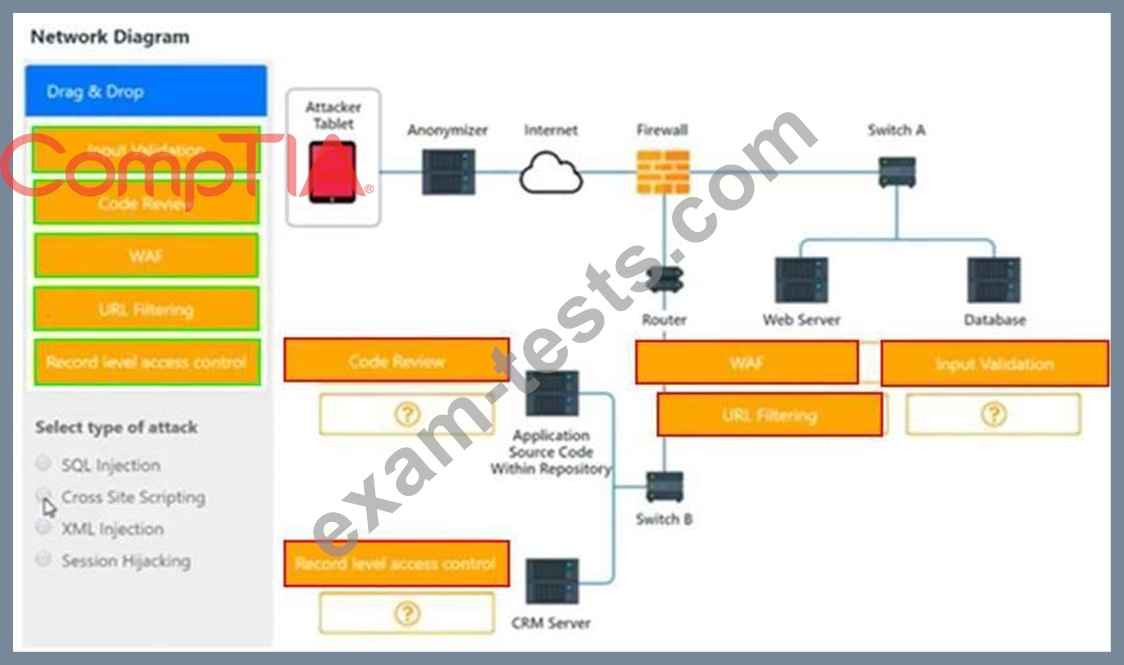
INSTRUCTIONS
You have been tasked to do the following:
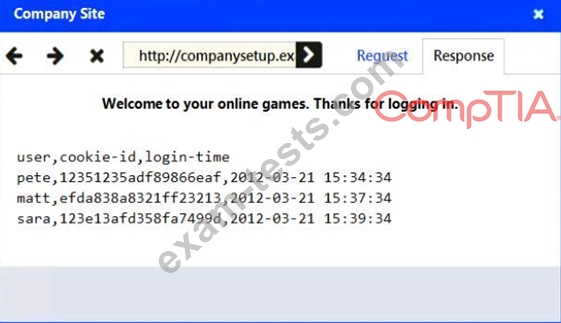
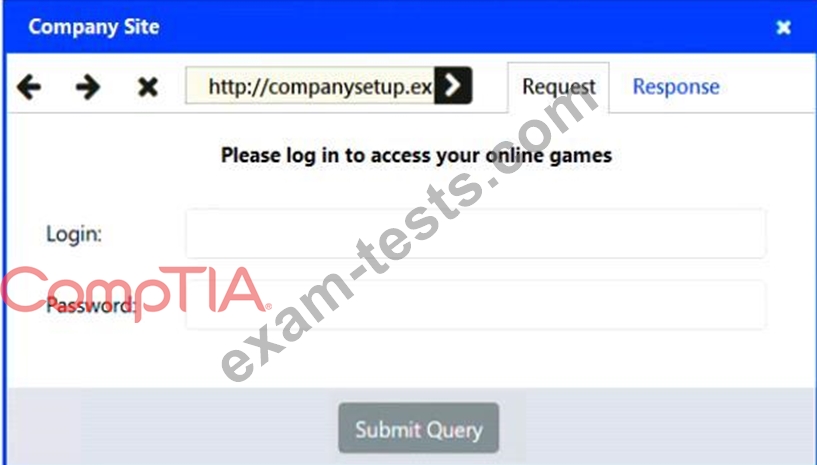
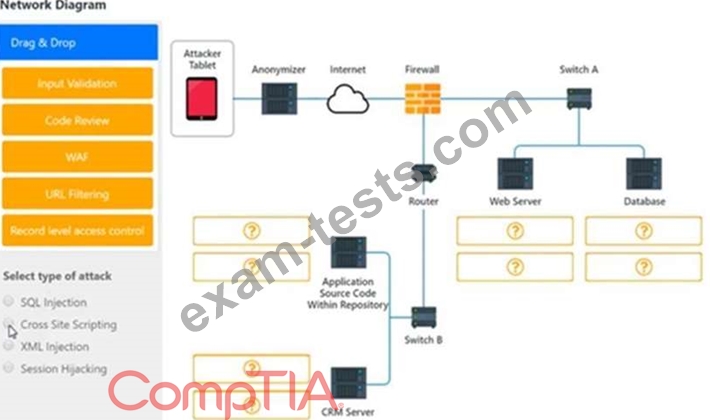
Identify the type of attack that is occurring on the network by clicking on the attacker's tablet and reviewing the output. (Answer Area 1) Identify which compensating controls should be implemented on the assets, in order to reduce the effectiveness of future attacks by dragging them to the correct server. (Answer area 2) All objects will be used, but not all placeholders may be filled. Objects may only be used once.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
INSTRUCTIONS
You have been tasked to do the following:
Identify the type of attack that is occurring on the network by clicking on the attacker's tablet and reviewing the output. (Answer Area 1) Identify which compensating controls should be implemented on the assets, in order to reduce the effectiveness of future attacks by dragging them to the correct server. (Answer area 2) All objects will be used, but not all placeholders may be filled. Objects may only be used once.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.



Question 98
The POODLE attack is an MITM exploit that affects:
Question 99
A systems administrator needs to configure an SSL remote access VPN according to the following organizational guidelines:
* The VPN must support encryption of header and payload.
* The VPN must route all traffic through the company's gateway.
Which of the following should be configured on the VPN concentrator?
* The VPN must support encryption of header and payload.
* The VPN must route all traffic through the company's gateway.
Which of the following should be configured on the VPN concentrator?
Question 100
It determining when it may be necessary to perform a credentialed scan against a system instead of a non-credentialed scanner requirements is MOST likely to influence this decision?