Question 86
DRAG DROP
Drag the items on the left to show the different types of security for the shown devices. Not all fields need to be filled. Not all items need to be used.
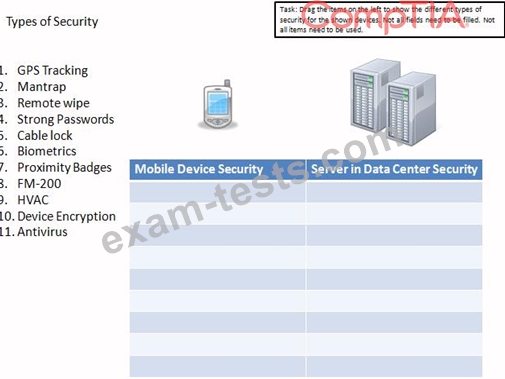
Drag the items on the left to show the different types of security for the shown devices. Not all fields need to be filled. Not all items need to be used.

Question 87
A penetration tester harvests potential usernames from a social networking site. The penetration tester then uses social engineering to attempt to obtain associated passwords to gain unauthorized access to shares on a network server. Which of the following methods is the penetration tester MOST likely using?
Question 88
Ann, a security analyst, wants to implement a secure exchange of email. Which of the following is the BEST option for Ann to implement?
Question 89
An audit found that an organization needs to implement job rotation to be compliant with regulatory requirements. To prevent unauthorized access to systems after an individual changes roles or departments, which of the following should the organization implement?
Question 90
After patching computers with the latest application security patches/updates, users are unable to open certain applications. Which of the following will correct the issue?

