Question 371
A systems administrator wants to replace the process of using a CRL to verify certificate validity. Which of the following would BEST suit the administrator's needs?
Question 372
A security administrator is reviewing the following report from an organization's patch management system that has only wired workstations which are utilized daily:
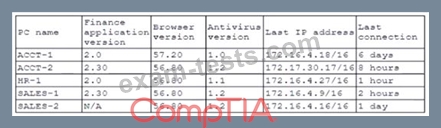
Which of the following is the GREATEST security concern for the administrator?

Which of the following is the GREATEST security concern for the administrator?
Question 373
Which of the following encryption methods does PKI typically use to securely project keys?
Question 374
A security architect is designing an enterprise solution for the sales force of a corporation which handles sensitive customer data. The solution must allow users to work from remote offices and support traveling users. Which of the following is the MOST appropriate control for the architect to focus onto ensure confidentiality of data stored on laptops?
Question 375
After a user reports stow computer performance, a systems administrator detects a suspicious file, which was installed as part of a freeware software package.
The systems administrator reviews the output below:

Based on the above information, which of the following types of malware was installed on the user's computer?
The systems administrator reviews the output below:

Based on the above information, which of the following types of malware was installed on the user's computer?

