Question 381
After successfully breaking into several networks and infecting multiple machines with malware. hackers contact the network owners, demanding payment to remove the infection and decrypt files. The hackers threaten to publicly release information about the breach if they are not paid. Which of the following BEST describes these attackers?
Question 382
A cybersecurity analyst is looking into the payload of a random packet capture file that was selected for analysis. The analyst notices that an internal host had a socket established with another internal host over a non-standard port.
Upon investigation, the origin host that initiated the socket shows this output:
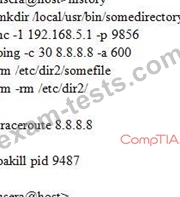
Given the above output, which of the following commands would have established the questionable socket?
Upon investigation, the origin host that initiated the socket shows this output:

Given the above output, which of the following commands would have established the questionable socket?
Question 383
A security analyst is reviewing the logs from a NGFWs automated correlation engine and sees the following:
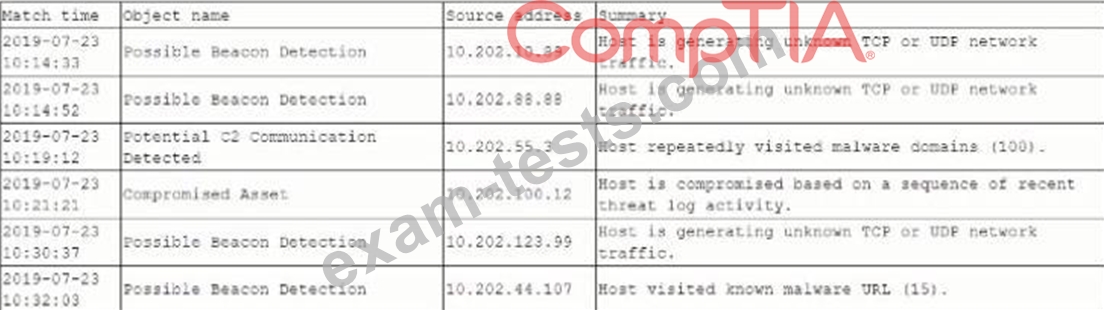
Which of the following should the analyst perform FIRST?

Which of the following should the analyst perform FIRST?
Question 384
Which of the following methods minimizes the system interaction when gathering information to conduct a vulnerability assessment of a router?
Question 385
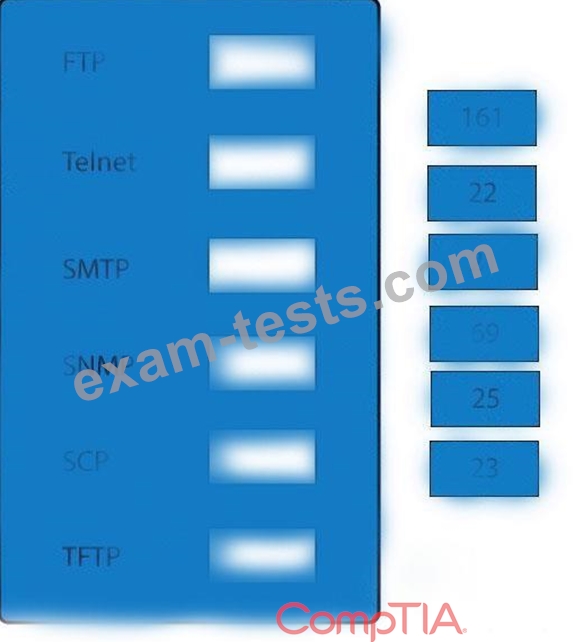
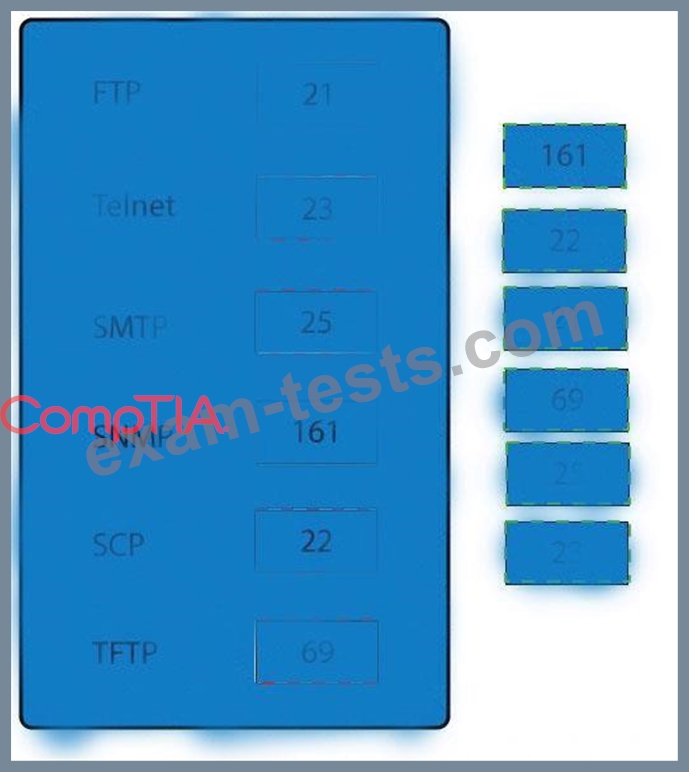
Drag and drop the correct protocol to its default port.