Question 441
A recent internal audit is forcing a company to review each internal business unit's VMs because the cluster they are installed on is in danger of running out of computer resources. Which of the following vulnerabilities exist?
Question 442
A security administrator is evaluating three different services: radius, diameter, and Kerberos.
Which of the following is a feature that is UNIQUE to Kerberos?
Which of the following is a feature that is UNIQUE to Kerberos?
Question 443
A security analyst investigate a report from an employee in the human resources (HR) department who is issues with Internal access. When the security analyst pull the UTM logs for the IP addresses in the HR group, the following activity is shown:
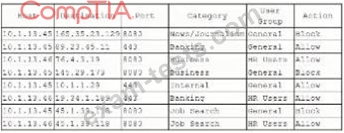
Which of the following actions should the security analyst take?

Which of the following actions should the security analyst take?
Question 444
A new intern in the purchasing department requires read access to shared documents. Permissions are normally controlled through a group called "Purchasing", however, the purchasing group permissions allow write access. Which of the following would be the BEST course of action?
Question 445
A company is executing a strategy to encrypt and sign all proprietary data in transit. The company recently deployed PKI services to support this strategy.
Which of the following protocols supports the strategy and employs certificates generated by the PKI?
(Choose three.)
Which of the following protocols supports the strategy and employs certificates generated by the PKI?
(Choose three.)

