Question 436
While monitoring the SIEM, a security analyst observes traffic from an external IP to an IP address of the business network on port 443. Which of the following protocols would MOST likely cause this traffic?
Question 437
A computer forensics team is performing an integrity check on key systems files. The team is comparing the signatures of original baseline les with the latest signatures. The original baseline was taken on March 2, 2016.
and was established to be clean of malware and uncorrupted. The latest tile signatures were generated yesterday. One file is known to be corrupted, but when the team compares the signatures of the original and latest ies, the team sees the Following:
Original: 2d da b1 4a fc f1 98 06 b1 e5 26 b2 df e5 5b 3e cb 83 e1
Latest: 2d da b1 4a 98 fc f1 98 bl e5 26 b2 df e5 5b 3e cb 83 e1
Which of the following is MOST likely the situation?
and was established to be clean of malware and uncorrupted. The latest tile signatures were generated yesterday. One file is known to be corrupted, but when the team compares the signatures of the original and latest ies, the team sees the Following:
Original: 2d da b1 4a fc f1 98 06 b1 e5 26 b2 df e5 5b 3e cb 83 e1
Latest: 2d da b1 4a 98 fc f1 98 bl e5 26 b2 df e5 5b 3e cb 83 e1
Which of the following is MOST likely the situation?
Question 438
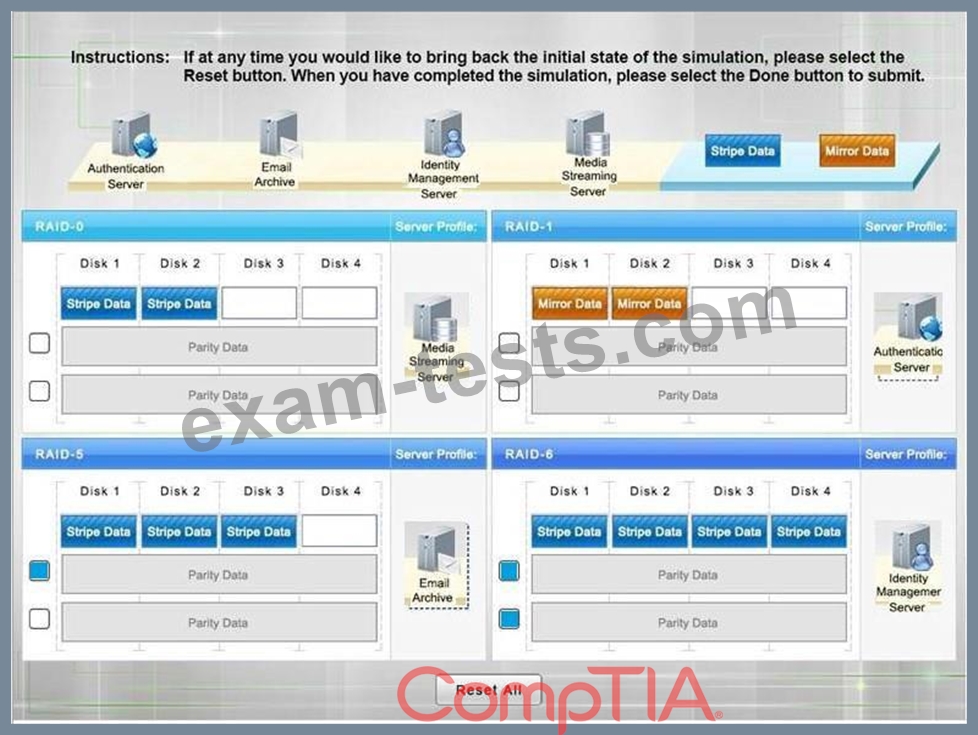
A security administrator is given the security and availability profiles for servers that are being deployed.
* Match each RAID type with the correct configuration and MINIMUM number of drives.
* Review the server profiles and match them with the appropriate RAID type based on integrity, availability, I/O, storage requirements. Instructions:
* All drive definitions can be dragged as many times as necessary
* Not all placeholders may be filled in the RAID configuration boxes
* If parity is required, please select the appropriate number of parity checkboxes
* Server profiles may be dragged only once
If at any time you would like to bring back the initial state of the simulation, please select the Reset button.
When you have completed the simulation, please select the Done button to submit. Once the simulation is submitted, please select the Next button to continue.
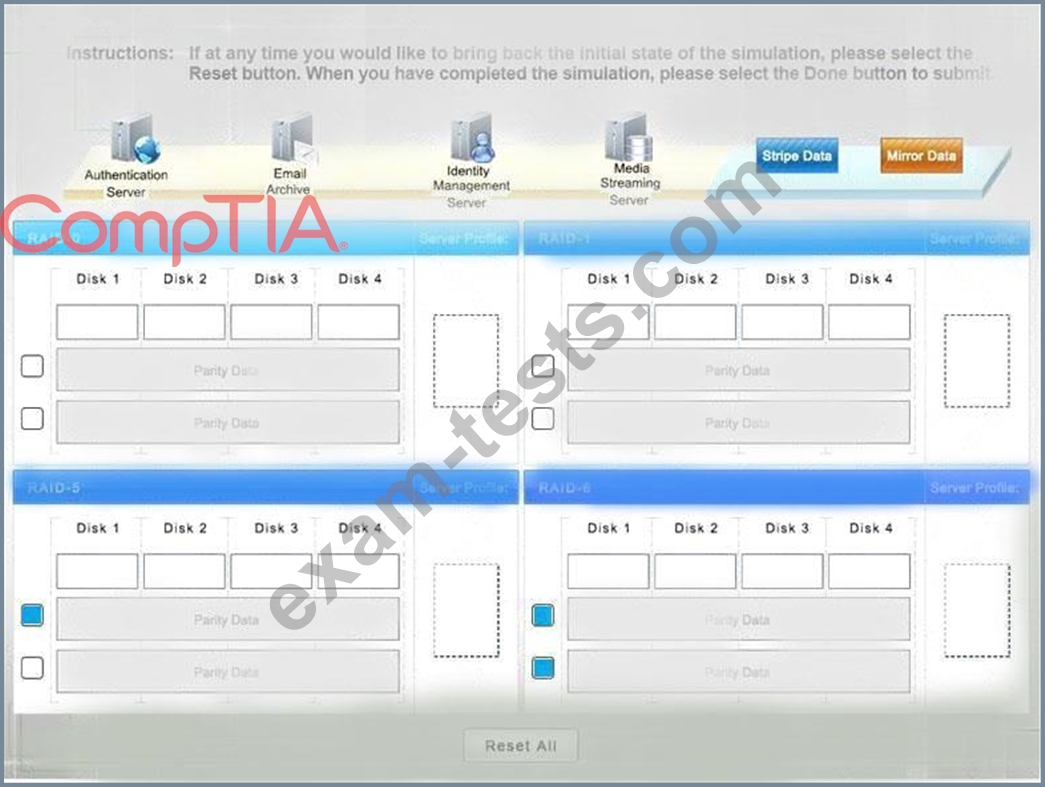
* Match each RAID type with the correct configuration and MINIMUM number of drives.
* Review the server profiles and match them with the appropriate RAID type based on integrity, availability, I/O, storage requirements. Instructions:
* All drive definitions can be dragged as many times as necessary
* Not all placeholders may be filled in the RAID configuration boxes
* If parity is required, please select the appropriate number of parity checkboxes
* Server profiles may be dragged only once
If at any time you would like to bring back the initial state of the simulation, please select the Reset button.
When you have completed the simulation, please select the Done button to submit. Once the simulation is submitted, please select the Next button to continue.

Question 439
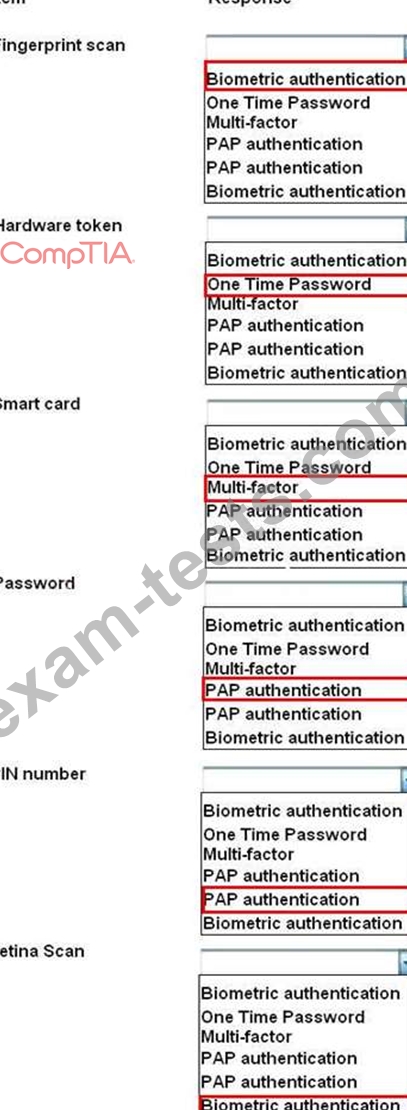
For each of the given items, select the appropriate authentication category from the drop down choices.
Select the appropriate authentication type for the following items:
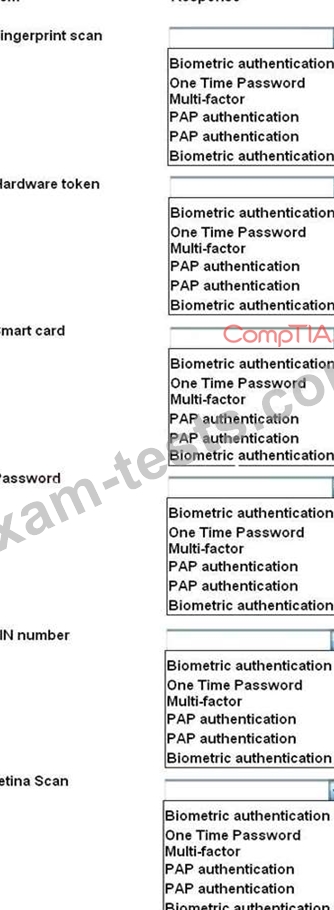
Select the appropriate authentication type for the following items:

Question 440
An auditor is reviewing the following output from a password-cracking tool:

Which of the following methods did the author MOST likely use?

Which of the following methods did the author MOST likely use?