Question 446
A systems administrator wants to configure an enterprise wireless solution that supports authentication over HTTPS and wireless encryption using AES. Which of the following should the administrator configure to support these requirements? (Select TWO).
Question 447
A vice president at a manufacturing organization is concerned about desktops being connected to the network.
Employees need to log onto the desktops' local account to verify that a product is being created within specifications; otherwise, the desktops should be as isolated as possible. Which of the following is the BEST way to accomplish this?
Employees need to log onto the desktops' local account to verify that a product is being created within specifications; otherwise, the desktops should be as isolated as possible. Which of the following is the BEST way to accomplish this?
Question 448
A security analyst is mitigating a pass-the-hash vulnerability on a Windows infrastructure. Given the requirement, which of the following should the security analyst do to MINIMIZE the risk?
Question 449
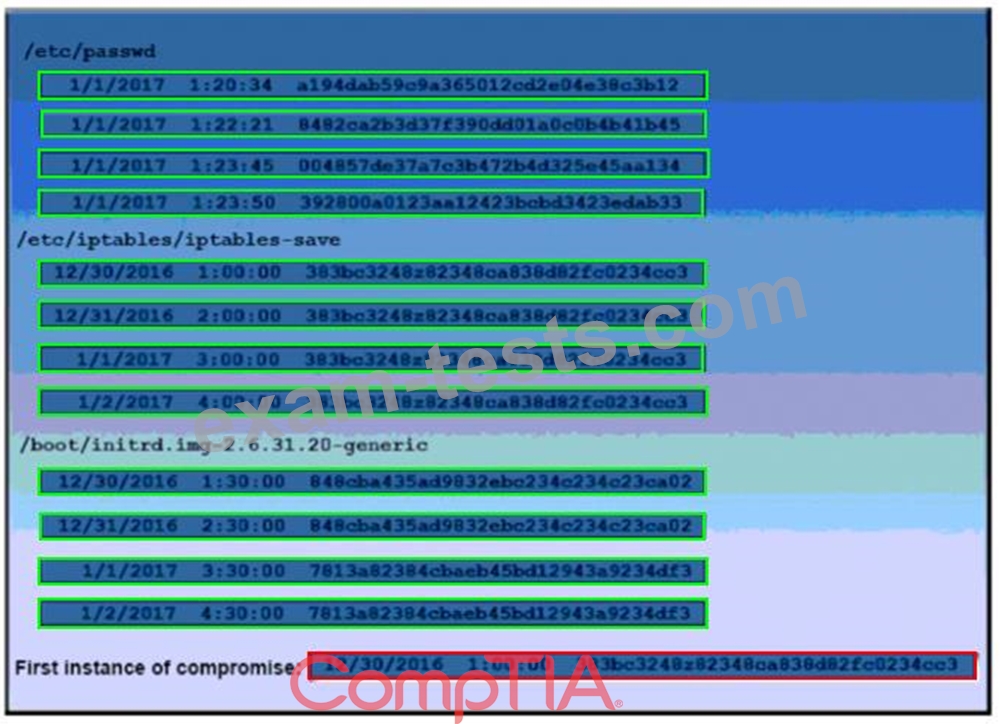
A security auditor is reviewing the following output from file integrity monitoring software installed on a very busy server at a large service provider. The server has not been updates since it was installed. Drag and drop the log entry that identifies the first instance of server compromise.


Question 450
A systems administrator is reviewing the following information from a compromised server:

Given the above information, which of the following processes was MOST likely exploited via a remote buffer overflow attack?

Given the above information, which of the following processes was MOST likely exploited via a remote buffer overflow attack?