Question 46
Which signature impacts network traffic by causing legitimate traffic to be blocked?
Question 47
Which category relates to improper use or disclosure of PII data?
Question 48
What are two social engineering techniques? (Choose two.)
Question 49
Refer to the exhibit.
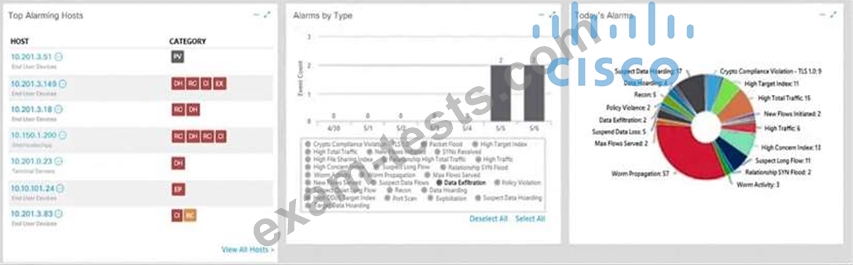
What is the potential threat identified in this Stealthwatch dashboard?

What is the potential threat identified in this Stealthwatch dashboard?
Question 50
Refer to the exhibit.
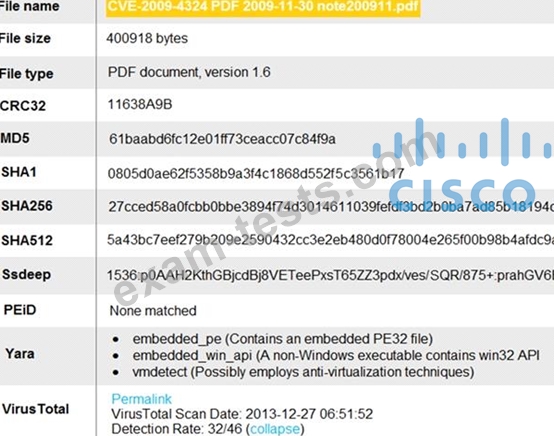
An engineer is analyzing this Cuckoo Sandbox report for a PDF file that has been downloaded from an email. What is the state of this file?

An engineer is analyzing this Cuckoo Sandbox report for a PDF file that has been downloaded from an email. What is the state of this file?

