Question 71
How does TOR alter data content during transit?
Question 72
A company receptionist received a threatening call referencing stealing assets and did not take any action assuming it was a social engineering attempt. Within 48 hours, multiple assets were breached, affecting the confidentiality of sensitive information. What is the threat actor in this incident?
Question 73
What is the impact of false positive alerts on business compared to true positive?
Question 74
Refer to the exhibit.
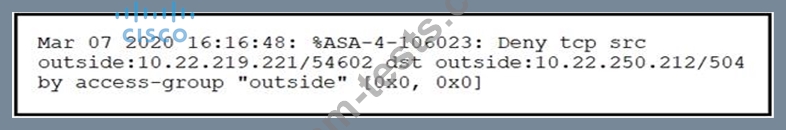
Which technology generates this log?

Which technology generates this log?
Question 75
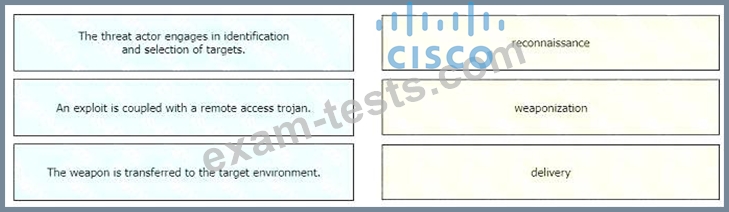
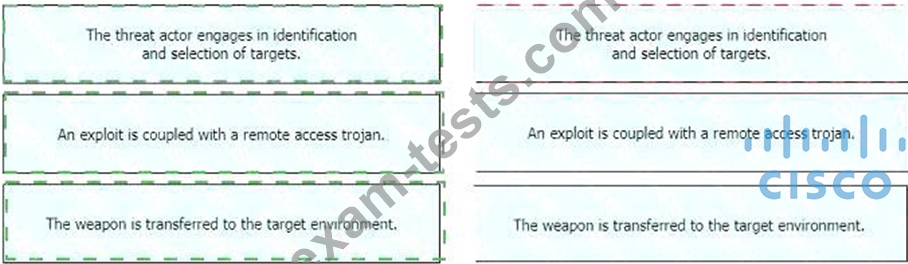
Drag and drop the definition from the left onto the phase on the right to classify intrusion events according to the Cyber Kill Chain model.