Question 61
Refer to the exhibit.
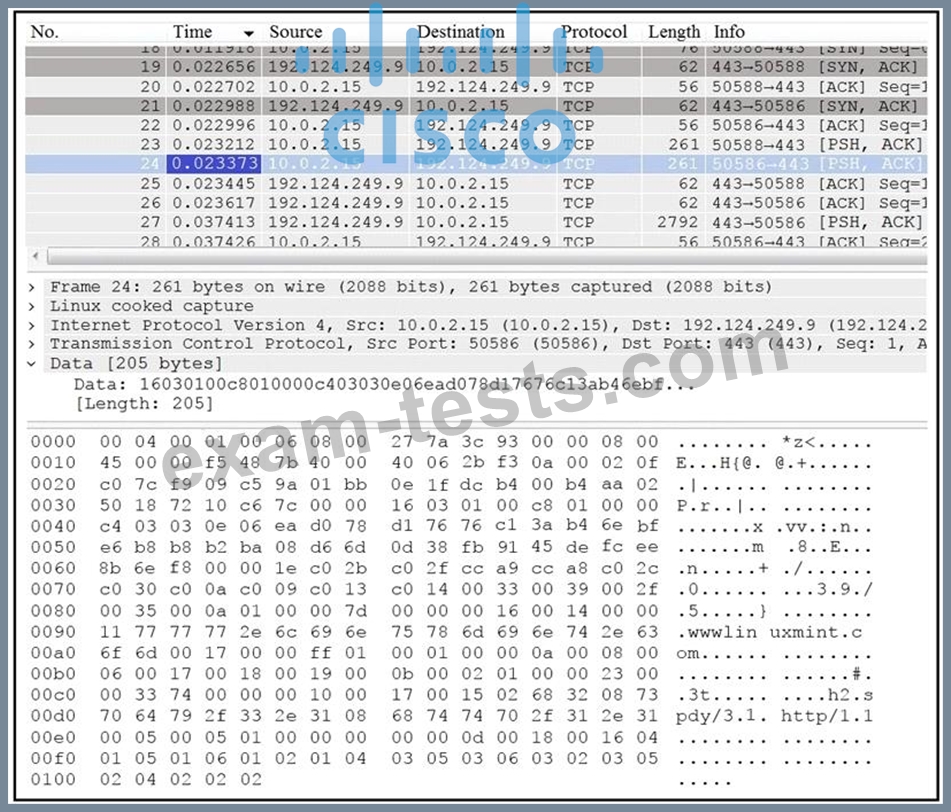
Which application protocol is in this PCAP file?

Which application protocol is in this PCAP file?
Question 62
How does an attack surface differ from an attack vector?
Question 63
Which of these describes SOC metrics in relation to security incidents?
Question 64
Drag and drop the security concept on the left onto the example of that concept on the right.
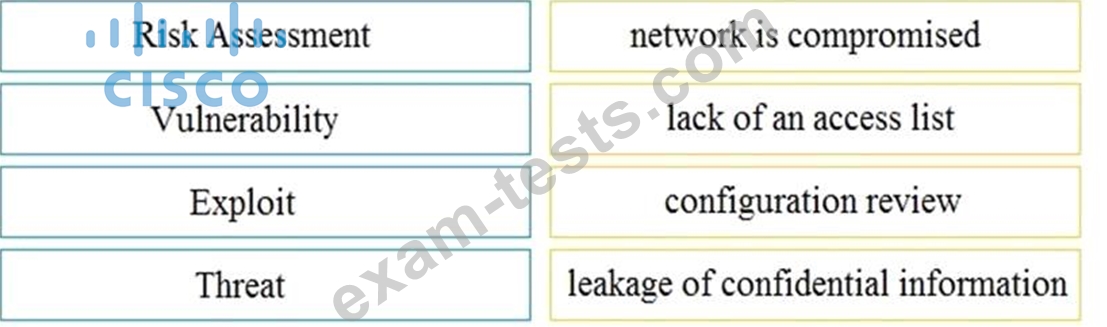

Question 65
An analyst is investigating a host in the network that appears to be communicating to a command and control server on the Internet. After collecting this packet capture, the analyst cannot determine the technique and payload used for the communication.
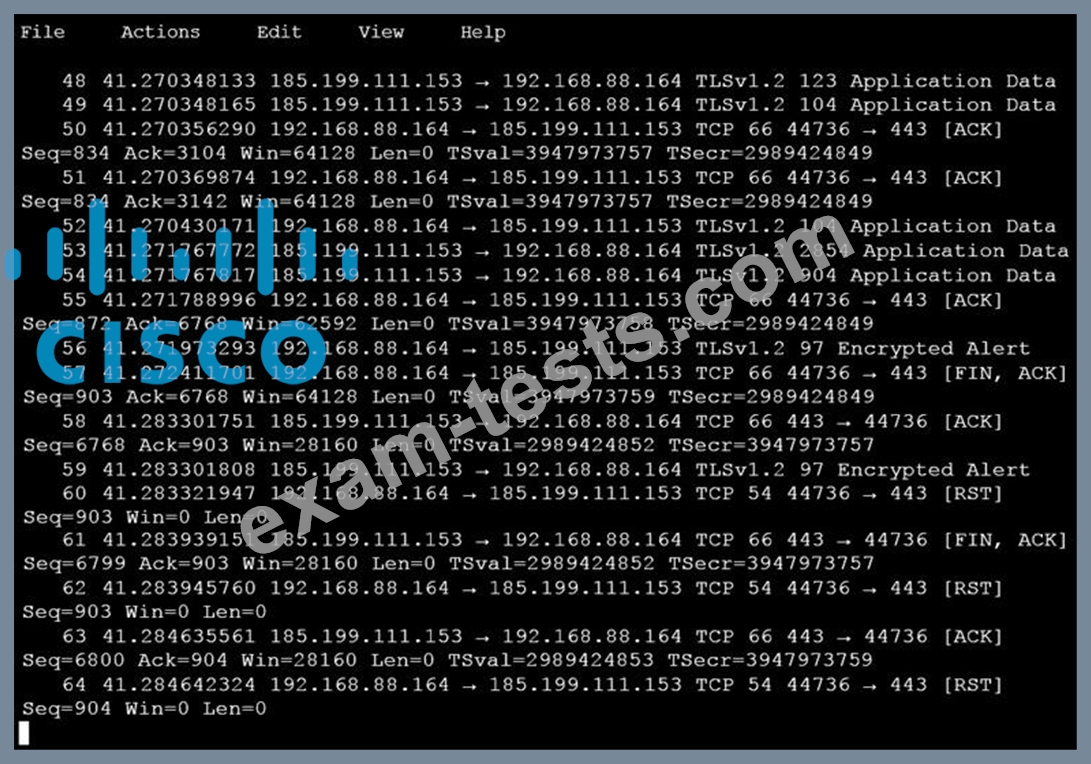
Which obfuscation technique is the attacker using?

Which obfuscation technique is the attacker using?


