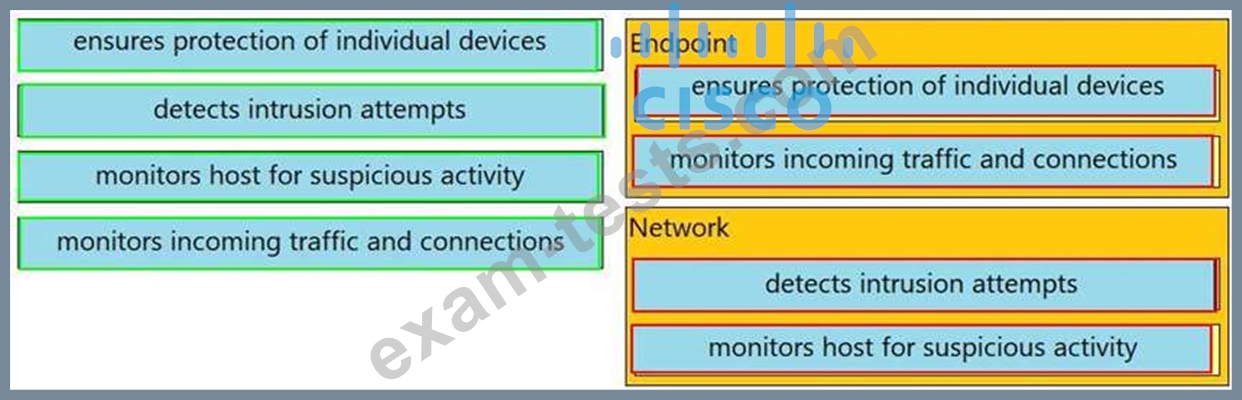
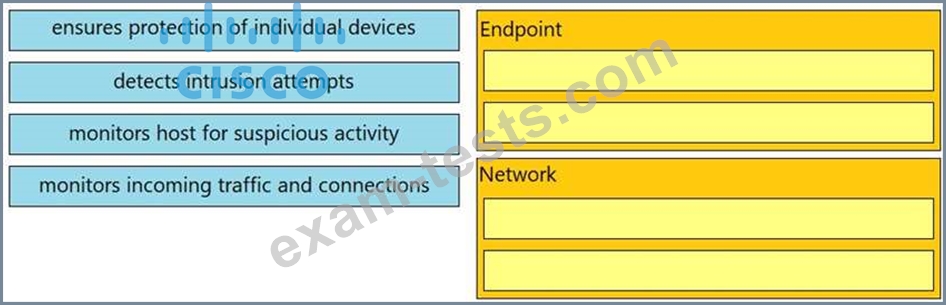
Question 51
Drag and drop the uses on the left onto the type of security system on the right.

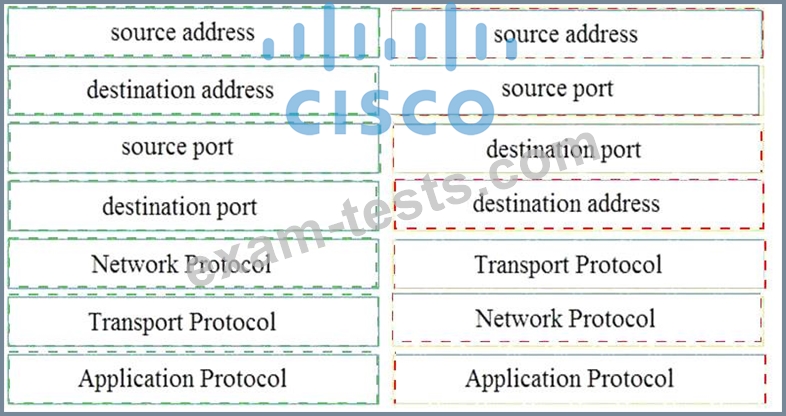
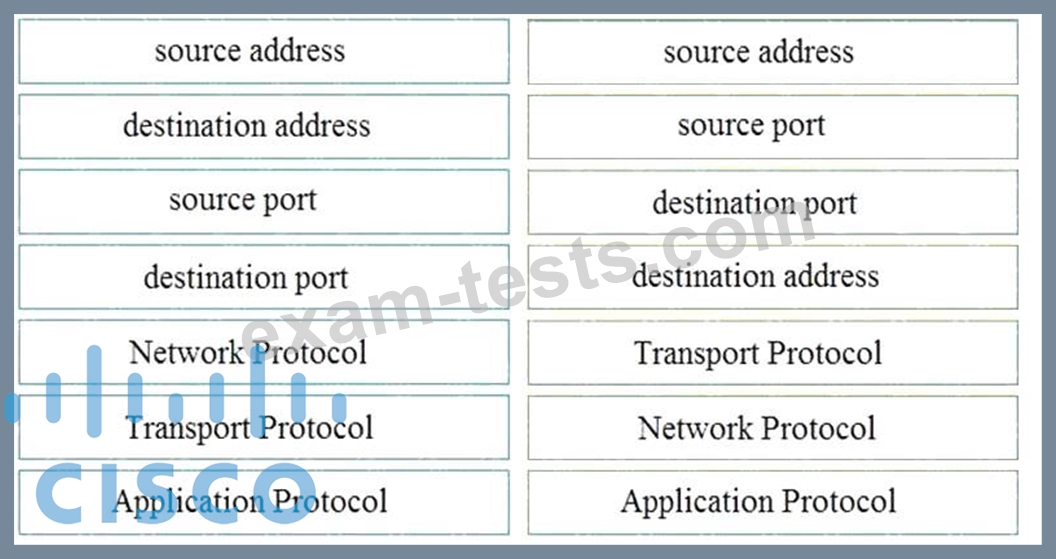
Question 52
Refer to the exhibit.
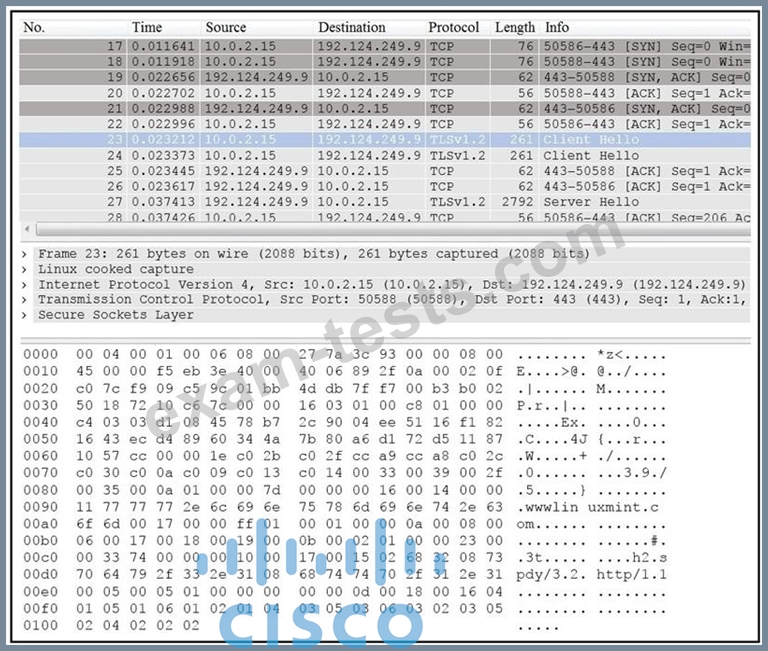
Drag and drop the element name from the left onto the correct piece of the PCAP file on the right.
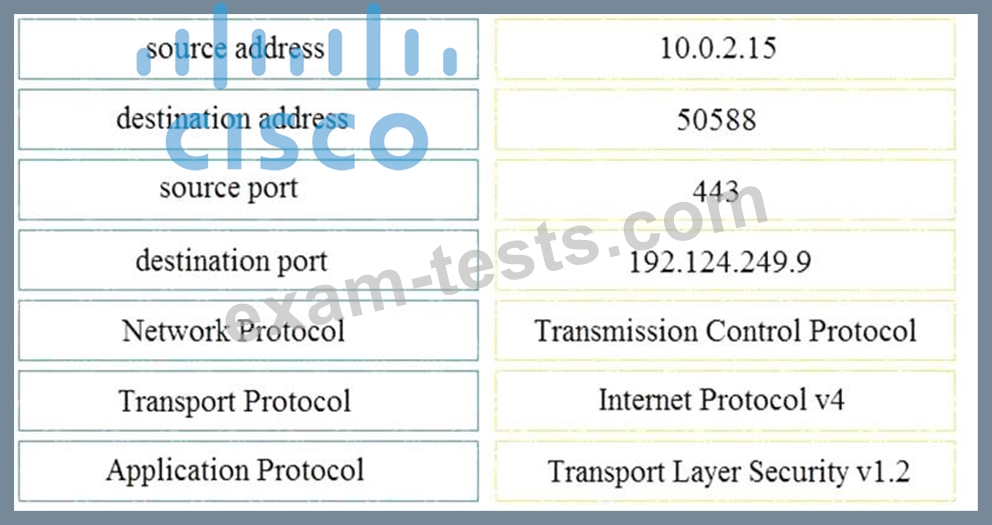

Drag and drop the element name from the left onto the correct piece of the PCAP file on the right.

Question 53
Refer to the exhibit.

Which event is occurring?

Which event is occurring?
Question 54
A security engineer deploys an enterprise-wide host/endpoint technology for all of the company's corporate PCs. Management requests the engineer to block a selected set of applications on all PCs.
Which technology should be used to accomplish this task?
Which technology should be used to accomplish this task?
Question 55
An employee reports that someone has logged into their system and made unapproved changes, files are out of order, and several documents have been placed in the recycle bin. The security specialist reviewed the system logs, found nothing suspicious, and was not able to determine what occurred. The software is up to date; there are no alerts from antivirus and no failed login attempts. What is causing the lack of data visibility needed to detect the attack?