Question 56
DRAG DROP
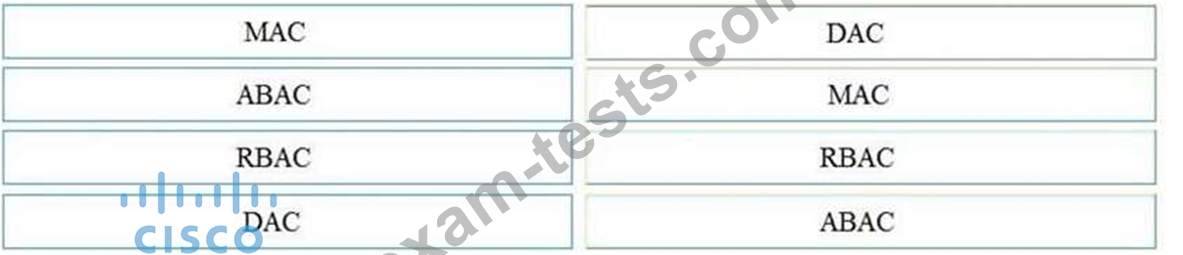
Drag and drop the access control models from the left onto the correct descriptions on the right.
Select and Place:
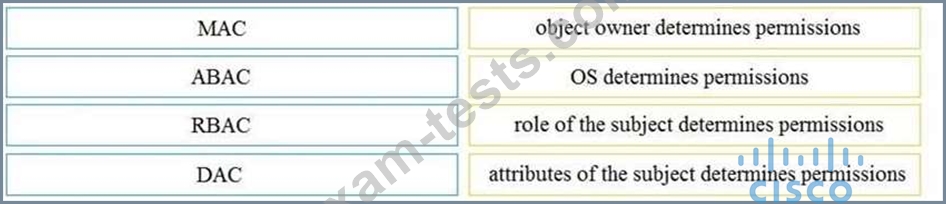
Drag and drop the access control models from the left onto the correct descriptions on the right.
Select and Place:

Question 57
What is an attack surface as compared to a vulnerability?
Question 58
Refer to the exhibit.
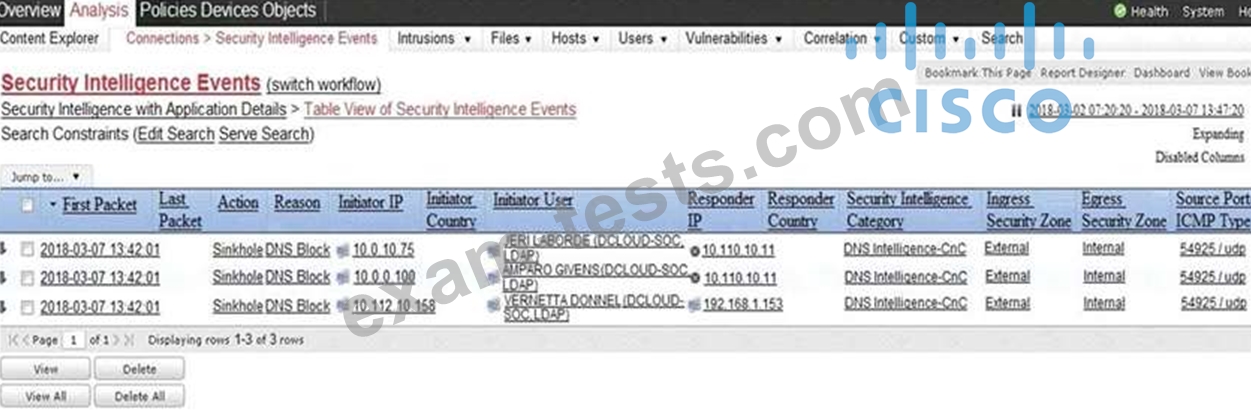
Which two elements in the table are parts of the 5-tuple? (Choose two.)

Which two elements in the table are parts of the 5-tuple? (Choose two.)
Question 59
Which data type is necessary to get information about source/destination ports?
Question 60
Which open-sourced packet capture tool uses Linux and Mac OS X operating systems?