Question 126
What is a difference between tampered and untampered disk images?
Question 127
Which security principle is violated by running all processes as root or administrator?
Question 128
Refer to the exhibit.
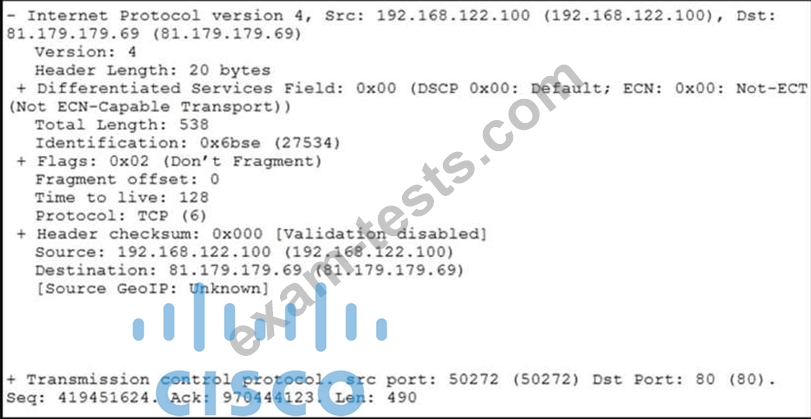
What should be interpreted from this packet capture?

What should be interpreted from this packet capture?
Question 129
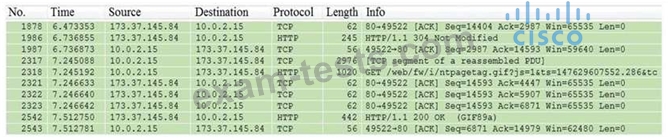
Refer to the exhibit. Which packet contains a file that is extractable within Wireshark?
Question 130
What is an attack surface as compared to a vulnerability?

