Question 81
Given the following output from a local PC:
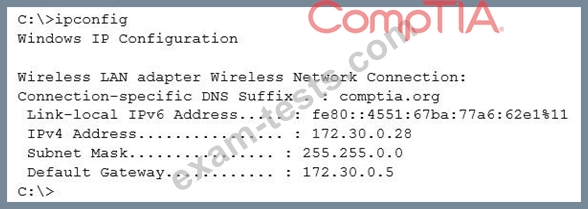
Which of the following ACLs on a stateful host-based firewall would allow the PC to serve an intranet website?

Which of the following ACLs on a stateful host-based firewall would allow the PC to serve an intranet website?
Question 82
The government is concerned with remote military missions being negatively being impacted by the use of technology that may fail to protect operational security. To remediate this concern, a number of solutions have been implemented, including the following:
* End-to-end encryption of all inbound and outbound communication, including personal email and chat sessions that allow soldiers to securely communicate with families.
* Layer 7 inspection and TCP/UDP port restriction, including firewall rules to only allow TCP port 80 and 443 and approved applications
* A host-based whitelist of approved websites and applications that only allow mission-related tools and sites
* The use of satellite communication to include multiple proxy servers to scramble the source IP address
Which of the following is of MOST concern in this scenario?
* End-to-end encryption of all inbound and outbound communication, including personal email and chat sessions that allow soldiers to securely communicate with families.
* Layer 7 inspection and TCP/UDP port restriction, including firewall rules to only allow TCP port 80 and 443 and approved applications
* A host-based whitelist of approved websites and applications that only allow mission-related tools and sites
* The use of satellite communication to include multiple proxy servers to scramble the source IP address
Which of the following is of MOST concern in this scenario?
Question 83
A security administrator wants to allow external organizations to cryptographically validate the company's domain name in email messages sent by employees. Which of the following should the security administrator implement?
Question 84
Which of the following would be used in forensic analysis of a compromised Linux system? (Select THREE).
Question 85
An analyst is investigating anomalous behavior on a corporate-owned, corporate-managed mobile device with application whitelisting enabled, based on a name string. The employee to whom the device is assigned reports the approved email client is displaying warning messages that can launch browser windows and is adding unrecognized email addresses to the "compose" window.
Which of the following would provide the analyst the BEST chance of understanding and characterizing the malicious behavior?
Which of the following would provide the analyst the BEST chance of understanding and characterizing the malicious behavior?

