Question 91
An information security manager is concerned that connectivity used to configure and troubleshoot critical
network devices could be attacked. The manager has tasked a network security engineer with meeting the
following requirements:
Encrypt all traffic between the network engineer and critical devices.

Segregate the different networking planes as much as possible.

Do not let access ports impact configuration tasks.

Which of the following would be the BEST recommendation for the network security engineer to present?
network devices could be attacked. The manager has tasked a network security engineer with meeting the
following requirements:
Encrypt all traffic between the network engineer and critical devices.

Segregate the different networking planes as much as possible.

Do not let access ports impact configuration tasks.

Which of the following would be the BEST recommendation for the network security engineer to present?
Question 92
An organization's email filler is an ineffective control and as a result employees have been constantly receiving phishing emails. As part of a security incident investigation a security analyst identifies the following:
1 An employee was working remotely when the security alert was triggered
2 An employee visited a number of uncategorized internet sites
3 A doc file was downloaded
4 A number of files were uploaded to an unknown collaboration site
Which of the following controls would provide the security analyst with more data to identify the root cause of the issue and protect the organization's information during future incidents?
1 An employee was working remotely when the security alert was triggered
2 An employee visited a number of uncategorized internet sites
3 A doc file was downloaded
4 A number of files were uploaded to an unknown collaboration site
Which of the following controls would provide the security analyst with more data to identify the root cause of the issue and protect the organization's information during future incidents?
Question 93
A company is in the process of implementing a new front end user interface for its customers, the goal is to provide them with more self-service functionality. The application has been written by developers over the last six months and the project is currently in the test phase.
Which of the following security activities should be implemented as part of the SDL in order to provide the MOST security coverage over the solution? (Select TWO).
Which of the following security activities should be implemented as part of the SDL in order to provide the MOST security coverage over the solution? (Select TWO).
Question 94
A developer emails the following output to a security administrator for review:
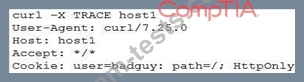
Which of the following tools might the security administrator use to perform further security assessment of this issue?

Which of the following tools might the security administrator use to perform further security assessment of this issue?
Question 95
An organization is evaluating options related to moving organizational assets to a cloud-based environment using an IaaS provider. One engineer has suggested connecting a second cloud environment within the organization's existing facilities to capitalize on available datacenter space and resources. Other project team members are concerned about such a commitment of organizational assets, and ask the Chief Security Officer (CSO) for input. The CSO explains that the project team should work with the engineer to evaluate the risks associated with using the datacenter to implement:

