Question 86
A security engineer is attempting to increase the randomness of numbers used in key generation in a system.
The goal of the effort is to strengthen the keys against predictive analysis attacks.
Which of the following is the BEST solution?
The goal of the effort is to strengthen the keys against predictive analysis attacks.
Which of the following is the BEST solution?
Question 87
A technician is reviewing the following log:
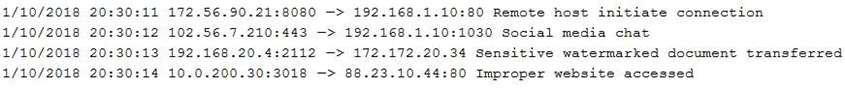
Which of the following tools should the organization implement to reduce the highest risk identified in this log?

Which of the following tools should the organization implement to reduce the highest risk identified in this log?
Question 88
A security manager looked at various logs while investigating a recent security breach in the data center from an external source. Each log below was collected from various security devices compiled from a report through the company's security information and event management server.
Logs:
Log 1:
Feb 5 23:55:37.743: %SEC-6-IPACCESSLOGS: list 10 denied 10.2.5.81 3 packets Log 2:
HTTP://www.company.com/index.php?user=aaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaa Log 3:
Security Error Alert
Event ID 50: The RDP protocol component X.224 detected an error in the protocol stream and has disconnected the client Log 4:
Encoder oe = new OracleEncoder ();
String query = "Select user_id FROM user_data WHERE user_name = ' "
+ oe.encode ( req.getParameter("userID") ) + " ' and user_password = ' "
+ oe.encode ( req.getParameter("pwd") ) +" ' ";
Vulnerabilities
Buffer overflow
SQL injection
ACL
XSS
Which of the following logs and vulnerabilities would MOST likely be related to the security breach? (Select TWO).
Logs:
Log 1:
Feb 5 23:55:37.743: %SEC-6-IPACCESSLOGS: list 10 denied 10.2.5.81 3 packets Log 2:
HTTP://www.company.com/index.php?user=aaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaa Log 3:
Security Error Alert
Event ID 50: The RDP protocol component X.224 detected an error in the protocol stream and has disconnected the client Log 4:
Encoder oe = new OracleEncoder ();
String query = "Select user_id FROM user_data WHERE user_name = ' "
+ oe.encode ( req.getParameter("userID") ) + " ' and user_password = ' "
+ oe.encode ( req.getParameter("pwd") ) +" ' ";
Vulnerabilities
Buffer overflow
SQL injection
ACL
XSS
Which of the following logs and vulnerabilities would MOST likely be related to the security breach? (Select TWO).
Question 89
As a security administrator, you are asked to harden a server running Red Hat Enterprise Server 5.5 64-bit.
This server is being used as a DNS and time server. It is not used as a database, web server, or print server. There are no wireless connections to the server, and it does not need to print.
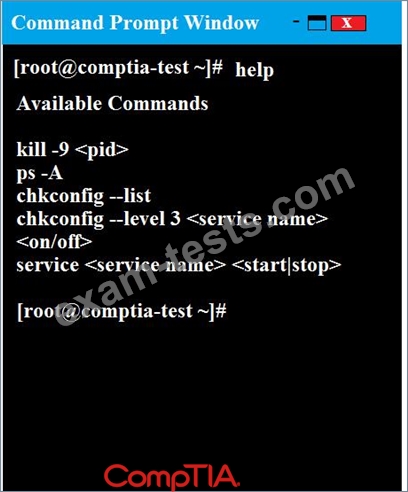
The command window will be provided along with root access. You are connected via a secure shell with root access.
You may query help for a list of commands.
Instructions:
You need to disable and turn off unrelated services and processes.
It is possible to simulate a crash of your server session. The simulation can be reset, but the server cannot be rebooted. If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.

See the explanation below
This server is being used as a DNS and time server. It is not used as a database, web server, or print server. There are no wireless connections to the server, and it does not need to print.
The command window will be provided along with root access. You are connected via a secure shell with root access.
You may query help for a list of commands.
Instructions:
You need to disable and turn off unrelated services and processes.
It is possible to simulate a crash of your server session. The simulation can be reset, but the server cannot be rebooted. If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.


See the explanation below
Question 90
The Chief Information Security Officer (CISO) at a large organization has been reviewing some security-related incidents at the organization and comparing them to current industry trends. The desktop security engineer feels that the use of USB storage devices on office computers has contributed to the frequency of security incidents. The CISO knows the acceptable use policy prohibits the use of USB storage devices. Every user receives a popup warning about this policy upon login. The SIEM system produces a report of USB violations on a monthly basis; yet violations continue to occur.
Which of the following preventative controls would MOST effectively mitigate the logical risks associated with the use of USB storage devices?
Which of the following preventative controls would MOST effectively mitigate the logical risks associated with the use of USB storage devices?

