Question 106
An engineer is evaluating the control profile to assign to a system containing PII, financial, and proprietary data.
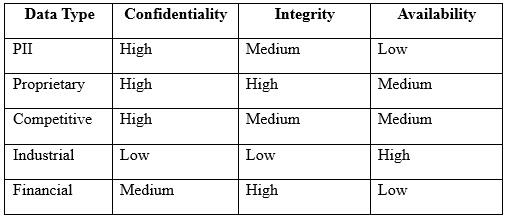
Based on the data classification table above, which of the following BEST describes the overall classification?

Based on the data classification table above, which of the following BEST describes the overall classification?
Question 107
Joe an application security engineer is performing an audit of an environmental control application He has implemented a robust SDLC process and is reviewing API calls available to the application During the review.
Joe finds the following in a log file.
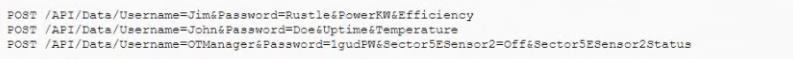
Which of the following would BEST mitigate the issue Joe has found?
Joe finds the following in a log file.

Which of the following would BEST mitigate the issue Joe has found?
Question 108
After being notified of an issue with the online shopping cart, where customers are able to arbitrarily change the price of listed items, a programmer analyzes the following piece of code used by a web based shopping cart.
SELECT ITEM FROM CART WHERE ITEM=ADDSLASHES($USERINPUT);
The programmer found that every time a user adds an item to the cart, a temporary file is created on the web server /tmp directory. The temporary file has a name which is generated by concatenating the content of the $USERINPUT variable and a timestamp in the form of MM-DD- YYYY, (e.g. smartphone-12-25-2013.tmp) containing the price of the item being purchased.
Which of the following is MOST likely being exploited to manipulate the price of a shopping cart's items?
SELECT ITEM FROM CART WHERE ITEM=ADDSLASHES($USERINPUT);
The programmer found that every time a user adds an item to the cart, a temporary file is created on the web server /tmp directory. The temporary file has a name which is generated by concatenating the content of the $USERINPUT variable and a timestamp in the form of MM-DD- YYYY, (e.g. smartphone-12-25-2013.tmp) containing the price of the item being purchased.
Which of the following is MOST likely being exploited to manipulate the price of a shopping cart's items?
Question 109
While attending a meeting with the human resources department, an organization's information security officer sees an employee using a username and password written on a memo pad to log into a specific service. When the information security officer inquires further as to why passwords are being written down, the response is that there are too many passwords to remember for all the different services the human resources department is required to use.
Additionally, each password has specific complexity requirements and different expiration time frames. Which of the following would be the BEST solution for the information security officer to recommend?
Additionally, each password has specific complexity requirements and different expiration time frames. Which of the following would be the BEST solution for the information security officer to recommend?
Question 110
A user asks a security practitioner for recommendations on securing a home network. The user recently
purchased a connected home assistant and multiple IoT devices in an effort to automate the home. Some
of the IoT devices are wearables, and other are installed in the user's automobiles. The current home
network is configured as a single flat network behind an ISP-supplied router. The router has a single IP
address, and the router performs NAT on incoming traffic to route it to individual devices.
Which of the following security controls would address the user's privacy concerns and provide the BEST
level of security for the home network?
purchased a connected home assistant and multiple IoT devices in an effort to automate the home. Some
of the IoT devices are wearables, and other are installed in the user's automobiles. The current home
network is configured as a single flat network behind an ISP-supplied router. The router has a single IP
address, and the router performs NAT on incoming traffic to route it to individual devices.
Which of the following security controls would address the user's privacy concerns and provide the BEST
level of security for the home network?

