Question 121
A Chief Security Officer (CSO) is reviewing the organization's incident response report from a recent incident. The details of the event indicate:
* A user received a phishing email that appeared to be a report from the organization's CRM tool.
* The user attempted to access the CRM tool via a fraudulent web page but was unable to access the tool.
* The user, unaware of the compromised account, did not report the incident and continued to use the CRM tool with the original credentials.
* Several weeks later, the user reported anomalous activity within the CRM tool.
* Following an investigation, it was determined the account was compromised and an attacker in another country has gained access to the CRM tool.
* Following identification of corrupted data and successful recovery from the incident, a lessons learned activity was to be led by the CSO.
Which of the following would MOST likely have allowed the user to more quickly identify the unauthorized use of credentials by the attacker?
* A user received a phishing email that appeared to be a report from the organization's CRM tool.
* The user attempted to access the CRM tool via a fraudulent web page but was unable to access the tool.
* The user, unaware of the compromised account, did not report the incident and continued to use the CRM tool with the original credentials.
* Several weeks later, the user reported anomalous activity within the CRM tool.
* Following an investigation, it was determined the account was compromised and an attacker in another country has gained access to the CRM tool.
* Following identification of corrupted data and successful recovery from the incident, a lessons learned activity was to be led by the CSO.
Which of the following would MOST likely have allowed the user to more quickly identify the unauthorized use of credentials by the attacker?
Question 122
A security engineer is working on a large software development project. As part of the design of the project, various stakeholder requirements were gathered and decomposed to an implementable and testable level. Various security requirements were also documented.
Organize the following security requirements into the correct hierarchy required for an SRTM.
Requirement 1: The system shall provide confidentiality for data in transit and data at rest.
Requirement 2: The system shall use SSL, SSH, or SCP for all data transport.
Requirement 3: The system shall implement a file-level encryption scheme.
Requirement 4: The system shall provide integrity for all data at rest.
Requirement 5: The system shall perform CRC checks on all files.
Organize the following security requirements into the correct hierarchy required for an SRTM.
Requirement 1: The system shall provide confidentiality for data in transit and data at rest.
Requirement 2: The system shall use SSL, SSH, or SCP for all data transport.
Requirement 3: The system shall implement a file-level encryption scheme.
Requirement 4: The system shall provide integrity for all data at rest.
Requirement 5: The system shall perform CRC checks on all files.
Question 123
A developer emails the following output to a security administrator for review:
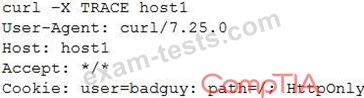
Which of the following tools might the security administrator use to perform further security assessment of this issue?

Which of the following tools might the security administrator use to perform further security assessment of this issue?
Question 124
Given the code snippet below:

Which of the following vulnerability types in the MOST concerning?

Which of the following vulnerability types in the MOST concerning?
Question 125
The Universal Research Association has just been acquired by the Association of Medical Business Researchers.
The new conglomerate has funds to upgrade or replace hardware as part of the acquisition, but cannot fund labor for major software projects.
Which of the following will MOST likely result in some IT resources not being integrated?
The new conglomerate has funds to upgrade or replace hardware as part of the acquisition, but cannot fund labor for major software projects.
Which of the following will MOST likely result in some IT resources not being integrated?

